The Get-ADGroup Cmdlet
The Get-ADGroup cmdlet enables IT admins to retrieve information about one or more Active Directory groups in the following ways:
- You can identify a group in many ways like its Distinguished name, GUID, SID or SAM account name.
- You can use Filter and LDAP Filter to fetch information about multiple groups from Active Directory.
- Additionally, you can define a group object variable, like $GroupObject.
Get-ADGroup searches some of the default properties of a group. To search for specific properties, use the Properties parameter.
Get-ADGroup: Syntax
Here is the syntax of this cmdlet:
Get-ADGroup [-AuthType ] [-Credential ] [-Identity] -Filter -LDAPFilter [-Properties <String[]>] [-ResultPageSize ] [-ResultSetSize ] [-SearchBase ] [-SearchScope ] [-Server ] [-ShowMemberTimeToLive]Get-ADGroup Cmdlet: Common Parameters
The most commonly used parameters of the Get-ADGroup cmdlet are:
- Credential
- AuthType
- Identity
- Filter
- LDAPFilter
- Partition
- Properties
- ResultPageSize
- ResultSetSize
- SearchBase
- SearchScope
- Server
Credential
By default, PowerShell uses the logged-on user’s credentials to run commands and scripts. You can use the Credential parameter to use alternate credentials. You can provide the username to this parameter and be prompted for the password. Or you can assign the credentials to a variable and use that variable with the command.
If the supplied credentials do not have the appropriate permissions in Active Directory to execute the cmdlet or script, PowerShell will return an error.
Authtype
The Authtype parameter specifies the type of authentication to employ. Here are the valid values:
- 0 or Negotiate — This is the standard authentication technique.
- 1 or Basic — This requires a Secure Sockets Layer (SSL) connection.
Identity
Identity is the only required parameter for the Get-ADGroup cmdlet. You can specify the group using any of the following:
- Distinguished name
- GUID
- SID
- Display name
- Canonical name
- SAM account name
The Identity parameter accepts pipeline input, but you cannot use wildcard characters.
Filter
To limit your search, you can use the Filter parameter to specify a query string using the PowerShell Expression Language. The PowerShell Expression Language syntax offers comprehensive type-conversion support for the values. In the following examples, note that the operator is positioned between the attribute and the value:
Get-ADGroup -Filter “GroupCategory -eq ’Security’”
Get-ADGroup -Filter “GroupScope -eq ‘Global’”
Most of your requirements should be met by the following operators:
| Operator | Meaning | Example |
| -eq | Equal to | Name -eq “G.U.Marketing” |
| -ne | Not equal to | GroupType -ne “-2147483640” |
| -gt | Greater than | Modified -gt “01-06-2021” |
| -ge | Greater than or equal | Created -ge “01-01-2018” |
| -lt | Less than | Modified -lt “01-02-2021” |
| -le | Less than or equal | Created -le “01-01-2018” |
| -like | Wildcard search | extensionAttribute1 -like “*” |
| -notlike | Wildcard search with negation | Name -notlike “Exchange*” |
| -and | And | Name -like “G.U.*” -and Name -like “*legal*” |
| -or | Or | Name -like “*marketing*” -or Name -like “*legal*” |
Please take note of the following in the examples above:
- Enclose value in single or double quotation marks.
- Use -like “” and -notlike “” to locate empty or full values.
Here are some additional examples:
Get-ADGroup -Filter 'Name -eq "Marketing"'
Get-ADGroup -Filter 'GroupType -ne "-2147583640"'
Get-ADGroup -Filter 'Modified -gt "01-07-2020"'
Get-ADGroup -Filter 'Created -ge "01-07-2017"'
Get-ADGroup -Filter 'Modified -lt "02-02-2020"'
Get-ADGroup -Filter 'Created -le "05-05-2016"'
Get-ADGroup -Filter 'extensionAttribute5 -like "*"'
Get-ADGroup -Filter 'Name -notlike "Exchange*"'
Get-ADGroup -Filter 'Name -like "F.M.*" -and Name -like "*HR*"'
Get-ADGroup -Filter 'Name -like "*finance*" -or Name -like "*Manager*"'
LDAPFilter
You can specify an LDAP query string to filter AD group objects.The datatype of this parameter is a string. You cannot use a pipeline with this parameter.
The Filter parameter also supports LDAP strings.
Partition
Use the Partition parameter to limit your search to a particular AD partition, which you specify using its distinguished name. The distinguished name should be one of the naming contexts of the current directory server.
If no value is provided, the default AD partition is searched. Below are some rules that determine the default value for the Partition parameter. The rules are assessed in the order shown below, and once a default value has been established, no more rules are examined.
- If the Identity parameter is set to a distinguished name, that distinguished name will be used as the default value for the Partition parameter.
- If an Active Directory provider drive is used to run the command, the default value of the Partition parameter is created automatically based on the drive’s current path.
- If neither of the previous two conditions apply, the target domain’s default partition or naming context is assigned as the default value for the Partition parameter.
Properties
By default, the Get-ADGroup cmdlet returns only some of the common properties of an object. To display additional properties, use the Properties parameter to specify the properties you want to see.
To display all the properties, use * (asterisk) with the Properties parameter.
To view specific properties, use a comma-separated list of the required property names.
To specify an extended property, use the property’s name.
For other properties not displayed by default, supply the LDAP display name of the property.
ResultPageSize
Use this parameter to specify how many objects should be shown on each page of the results. Specify the value as int32. The default is 256. This parameter does not accept wildcard characters or pipeline input.
ResultSetSize
Use this parameter to specify the maximum number of objects that the search should return. Specify the value as Int32. This parameter does not accept wildcard characters or pipeline input.
SearchBase
Use this parameter to limit your search to a specific OU, which you must specify using its distinguished name. If this parameter is not used, PowerShell runs the cmdlet for the target domain.
SearchScope
Use this parameter to limit the scope of your search within the OU defined using the SearchBase parameter. There are three possible values for this parameter:
0 or Base — Search only the base OU.
1 or OneLevel — Search the base OU and its immediate child OUs.
2 or Subtree — Search in the base OU and all its sub-OUs.
Server
Using this parameter, you can limit the search to a specified instance or ADDS (Active Directory Domain Services) server. You can use the fully qualified domain name or the NetBIOS name of the directory service server, or the port with FQDN.
Examples of the Get-ADGroup Cmdlet
Here are some examples of how you can use the Get-ADGroup cmdlet:
- Display the Default Properties of a Group
- Display Information About All Groups
- Get All the Properties of a Group
- Find All Groups with Similar Names
- Search for a Group by SAMAccountName
- Search for a Group by SID (Security Identifier)
- Search for a Group by Specifying Part of Its Name
- Count the AD Groups in the Domain
- Search for All Groups Managed by a Specific User
- Search by Group Type and Group Scope
- Search for Groups in a Particular OU
- Search for Groups in an OU and Its Sub-OUs
- Search for Groups on a Different Server
- Search for Groups using an LDAP Filter
- Export the Results to CSV Format
Display the Default Properties of a Group
Use the following command to display the default properties of the Administrators group:
Get-ADGroup -Identity Administrators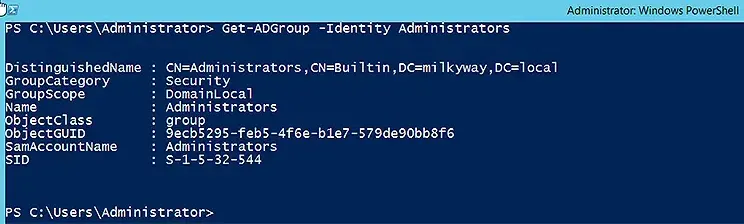
Display Information About All Groups
To display basic information about all groups, use the wildcard character (*) with the Filter parameter:
Get-ADGroup -Filter *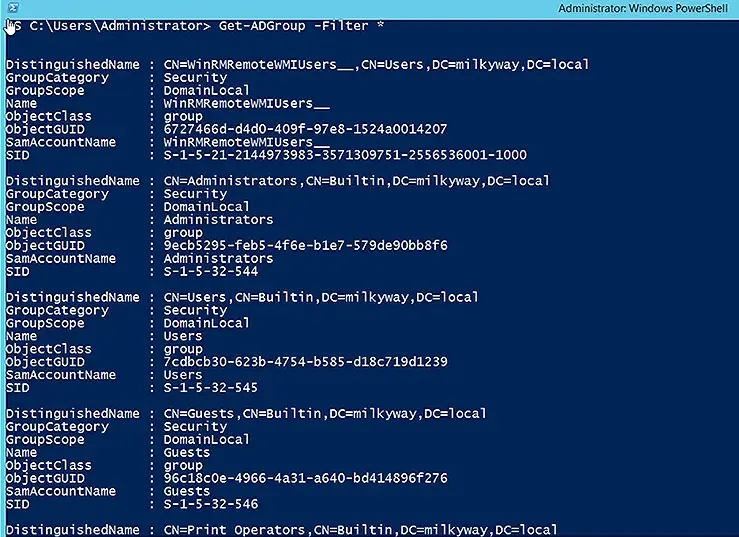
Get All the Properties of a Group
To see all the properties of a groups, use the Properties parameter with the wildcard character (*):
Get-ADGroup -Identity Administrators -Properties *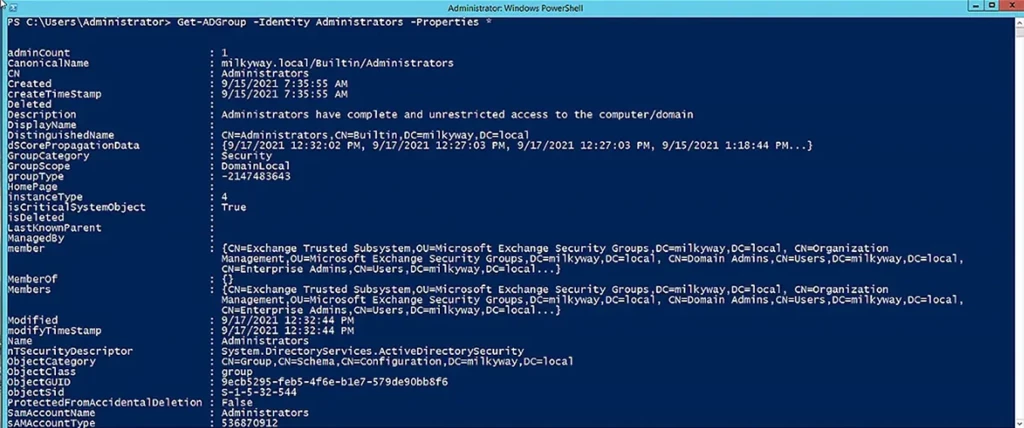
Find All Groups with Similar Names
To find all groups with the word “Sales” in their name, use the following cmdlet:
Get-ADGroup -filter {name -like '*Sales*'} | Select name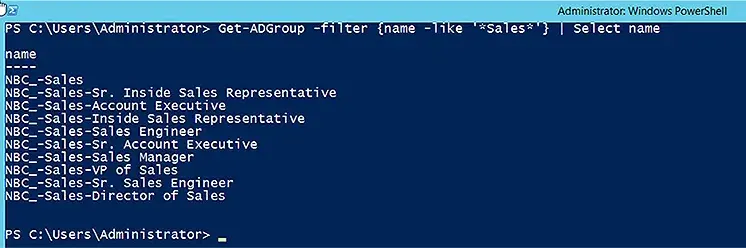
Search for a Group by SAMAccountName
To search for a group by its SAMAccountName, use this command:
Get-ADGroup -Identity "NBC Corp"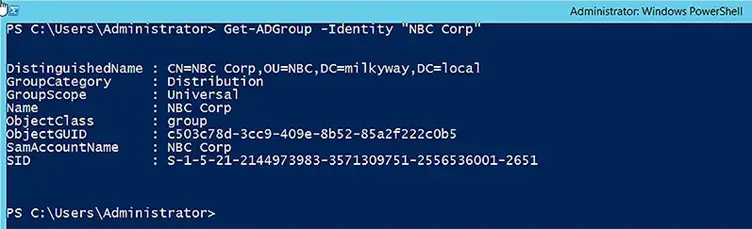
Search for a Group by SID (Security Identifier)
SIDs are used to store group permissions in access control lists (ACLs). To search for a group with a specific SID, use the following command. Note that we have used the Properties parameter to show the group’s membership as well as its default properties.
Get-ADGroup -Identity S-1-5-21-2144973983-3571309751-2556536001-2690 -Properties member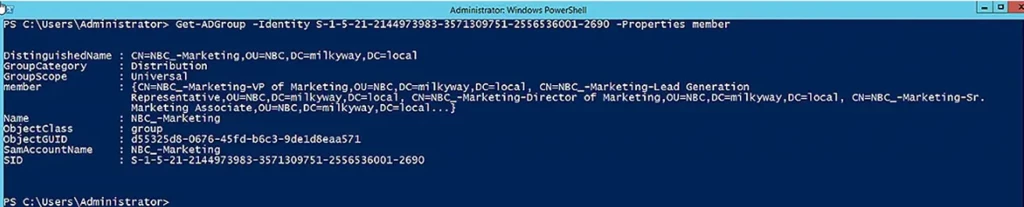
Search for a Group by Specifying Part of Its Name
The command below searches for groups using some of the Filter operators described earlier. The Properties parameter is used to include the group’s name, mail, and membership in the results.
Get-ADGroup -Filter "name -like '*finance*'" -Properties * | select name,mail,member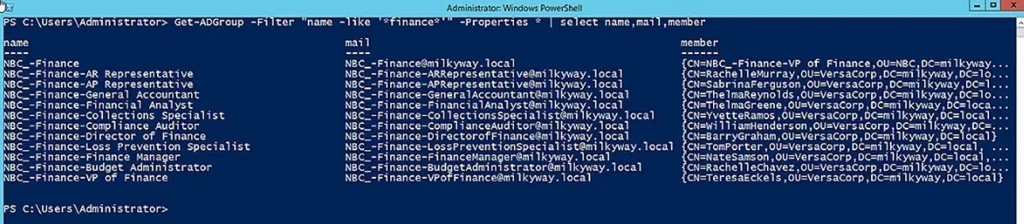
Count the AD Groups in the Domain
If you want to get the total count of group objects in the domain, use the Get-ADGroup cmdlet with the Count command, as shown below. To retrieve all the groups in the domain, we have used the Filter parameter with the wildcard character (*).
(Get-ADGroup -Filter '*').Count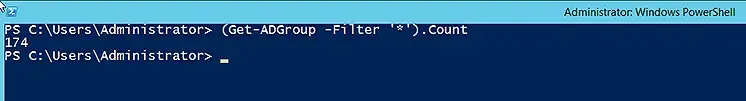
Search for All Groups Managed by a Specific User
To find all groups owned by a specific user, such as the administrator, use the following command:
Get-ADGroup -Filter 'managedby -eq "administrator"'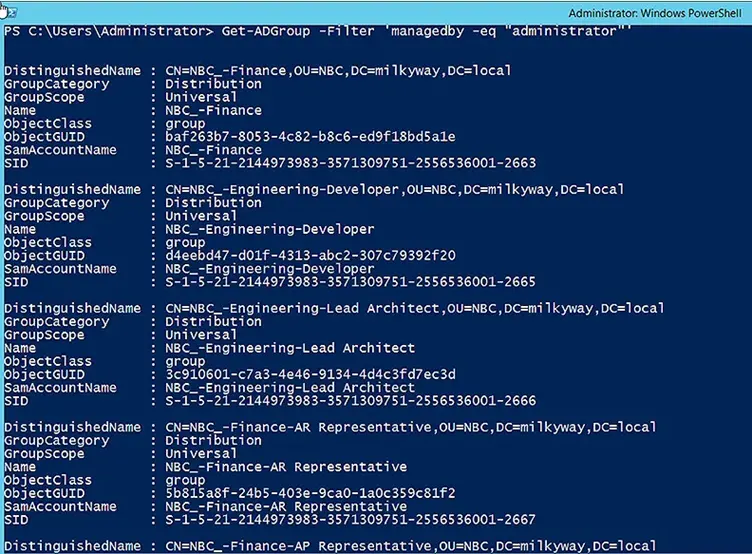
Notice that the results include all the default properties. When there are a large number of groups returned, it becomes difficult to analyze the details. Accordingly, the command below uses the Select parameter to limit the results to the name and distinguished name of the groups:
Get-ADGroup -Filter 'managedby -eq "administrator"' -Properties * | select Name,distinguishedname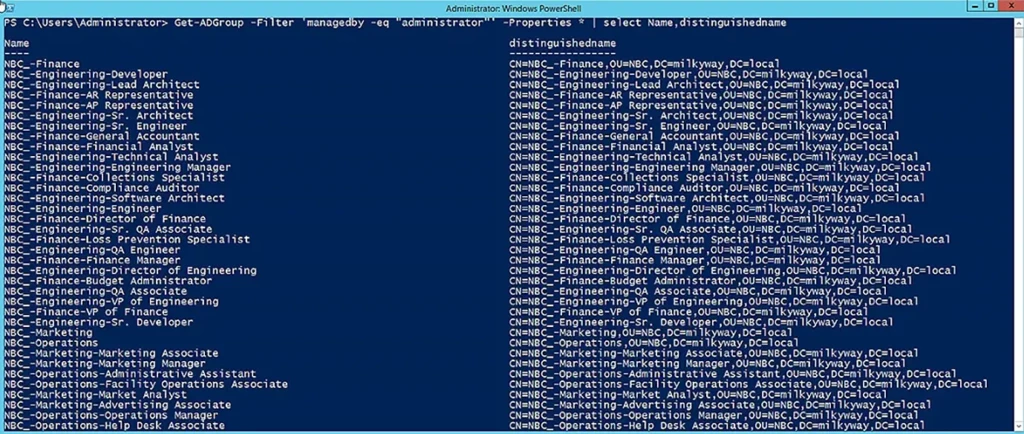
Search by Group Type and Group Scope
If you want to search for groups based on their group type (security or distribution) and then further filter them by group scope (universal, global, or domain local), you can use the following cmdlet. The Select parameter limits the results to just the group names.
Get-ADGroup -Filter 'GroupCategory -eq "Security" -and GroupScope -ne "DomainLocal"' -Properties * | select name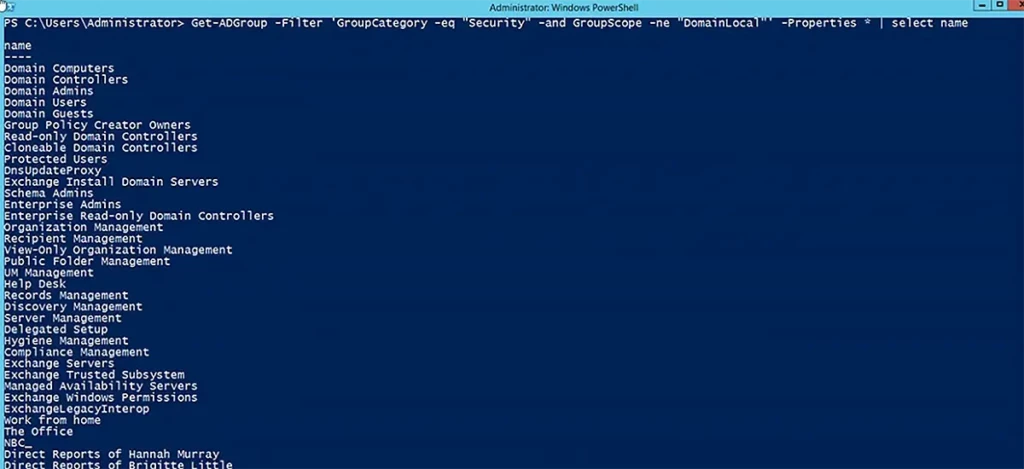
Search for Groups in a Particular OU
The following command uses the SearchBase parameter to limit the search to the OU specified by its distinguished name:
Get-ADGroup -Filter "GroupScope -eq 'DomainLocal'" -SearchBase "OU=NBC,DC=milkyway,DC=local" | select name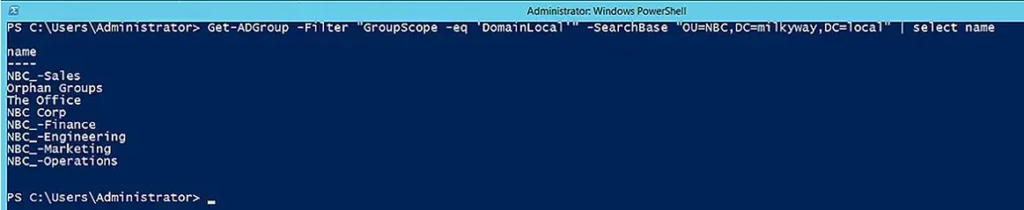
Search for Groups in an OU and Its Sub-OUs
The following command searches for groups in a particular OU and its immediate child OUs:
Get-ADGroup -Filter * -SearchBase "OU=BaseOU,DC=milkyway,DC=local" -SearchScope OneLevel | select name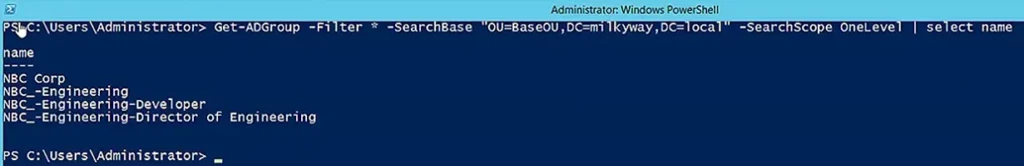
And this command searches for groups in a particular OU and all its sub-OUs:
Get-ADGroup -Filter * -SearchBase "OU=BaseOU,DC=milkyway,DC=local" -SearchScope Subtree | select name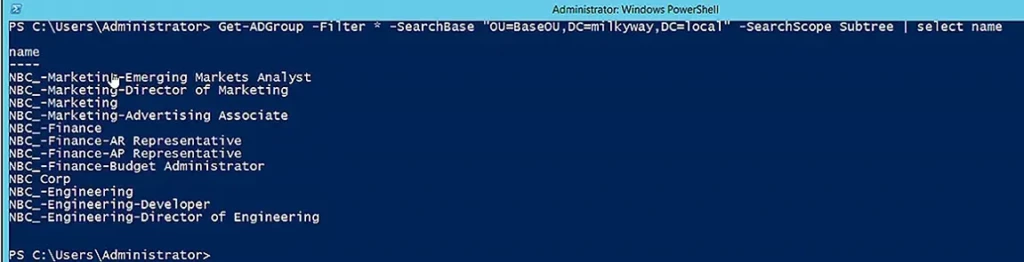
Search for Groups on a Different Server
If you want to search for group objects on a particular domain controller, you can use the Server parameter as shown below:
Get-ADGroup -Filter * -SearchBase "OU=BaseOU,DC=milkyway,DC=local" -Server dcexch2013.milkyway.local | select name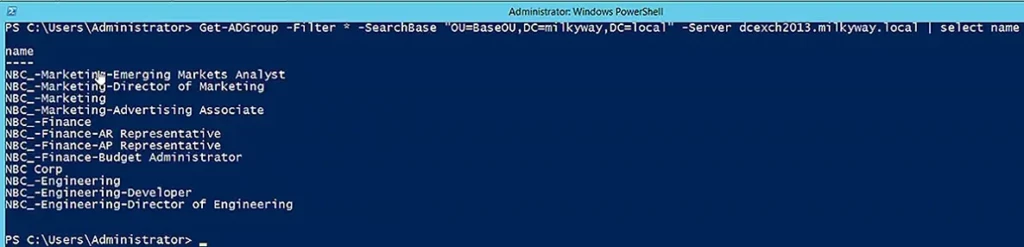
Search for Groups using an LDAP Filter
The following command searches for groups using an LDAP filter. We have used the SearchBase and SearchScope parameters to further limit the search.
Get-ADGroup -LDAPFilter "(name=NBC*)" -SearchScope Subtree -SearchBase "OU=BaseOU,DC=milkyway,DC=local" | select name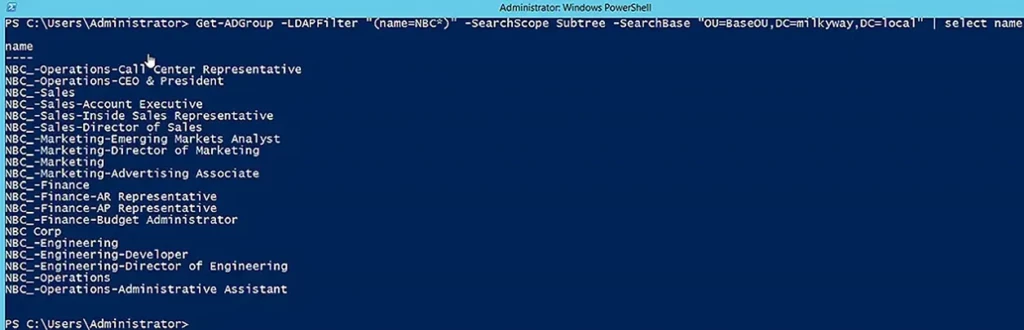
Export the Results to CSV Format
All the cmdlets we have shown display their results in PowerShell. Here is another example:
Get-ADGroup -Filter "name -like 'NBC*'" -Properties * | select name,mail,groupscope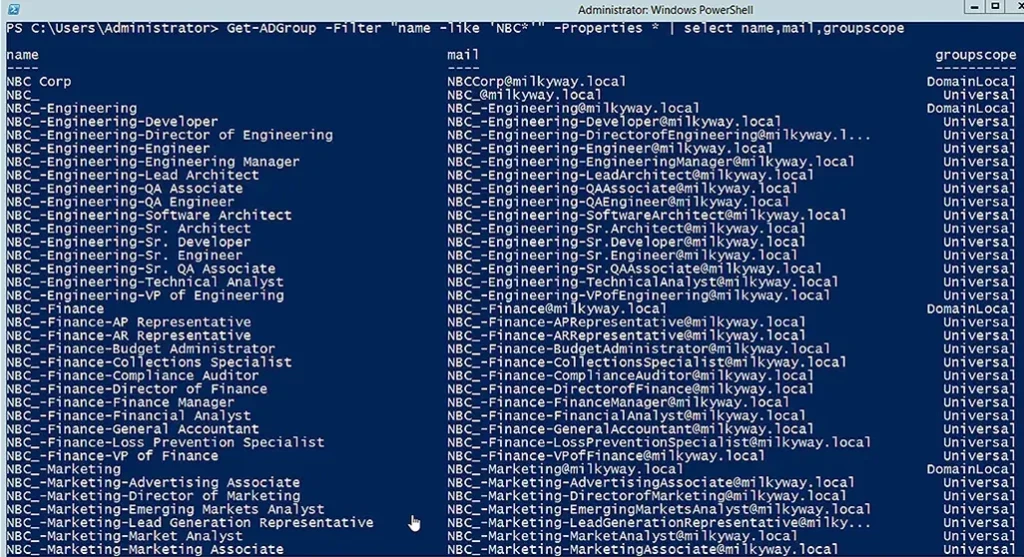
To save the results of the preceding command to a CSV file, simply add Export-CSV and the path and name of the CSV file:
Get-ADGroup -Filter "name -like 'NBC*'" -Properties * | select name,mail,groupscope | Export-CSV C:\TestFolder\GroupsResult.csv
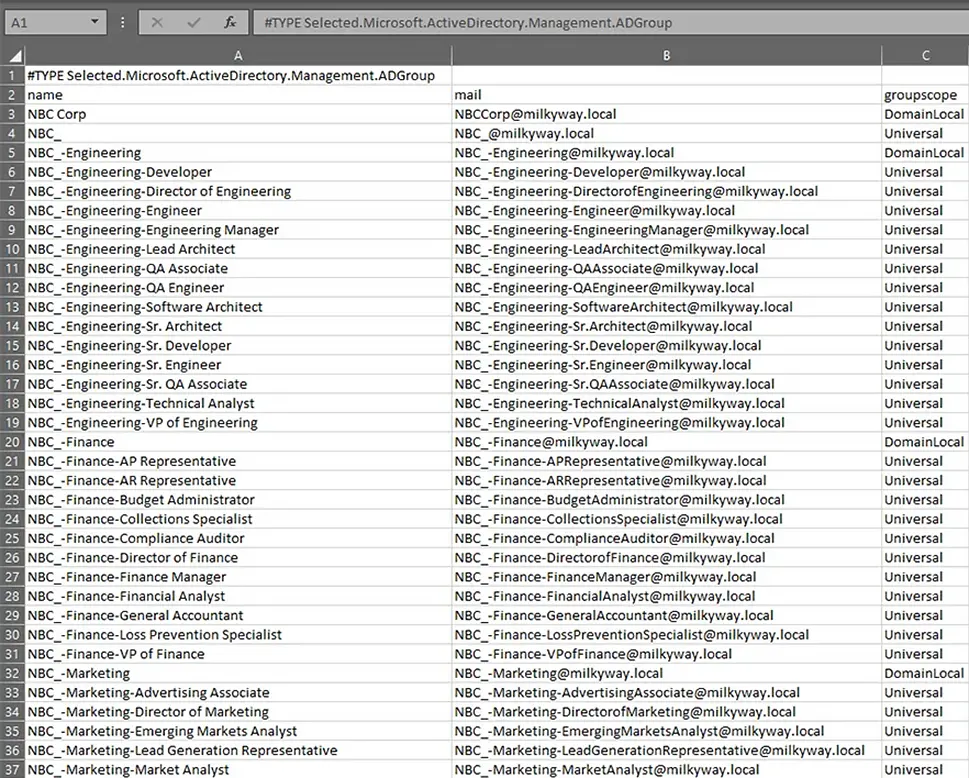
Here is a screenshot of the results in the form of a CSV file:
Below is another example of exporting the distinguished names of the groups to CSV:
Get-ADGroup -Filter "name -like 'NBC*'" -Properties * | select name,mail,distinguishedname | Export-CSV C:\TestFolder\GroupsResult.csv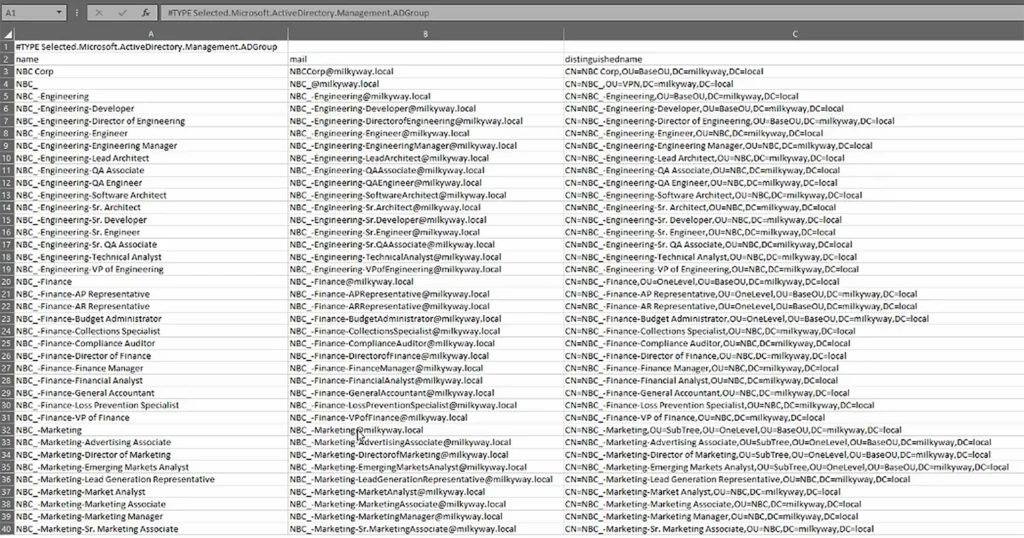
Netwrix GroupID
While PowerShell enables you to search for groups, learning all the cmdlets and creating scripts is time-consuming and error-prone. Netwrix GroupID provides a web-based interface that simplifies user and group management tasks for Active Directory administrators, and admins can even empower business users to update their own profiles and manage their own groups.
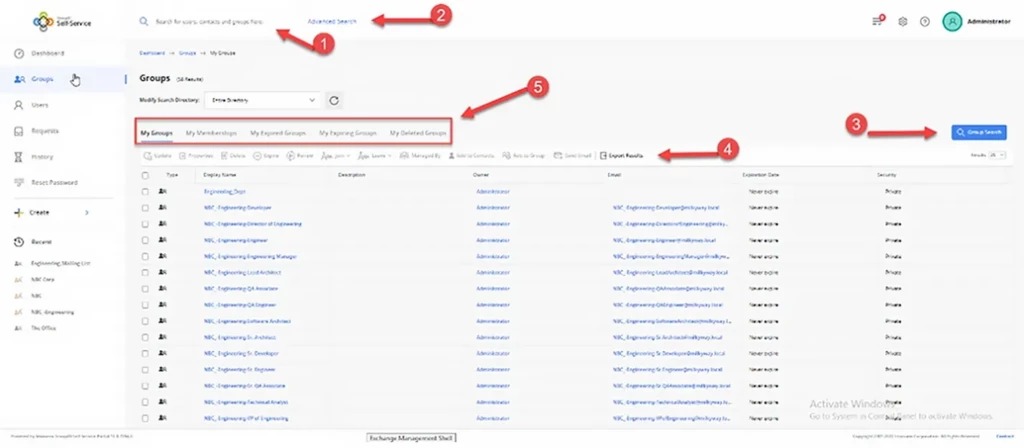
Here are the key things to know about the group search functionality:
- You can quickly search for user, group and contact objects by name, display name or canonical name, as shown here:
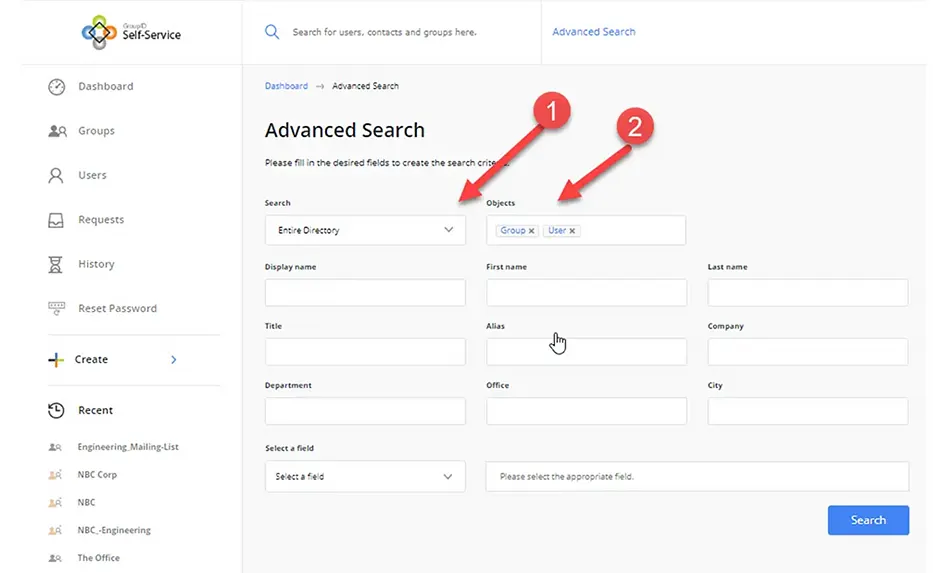
- The Advanced Search option enables you to narrow down the search, limit the object scope and search by additional properties:
- There is search functionality specifically for groups.
- You can easily export the results.
- Search results are sorted into My Groups, My Memberships, My Expiring Groups, My Expired Groups and My Deleted Groups, with a separate tab dedicated to each type.
GroupID Management Shell
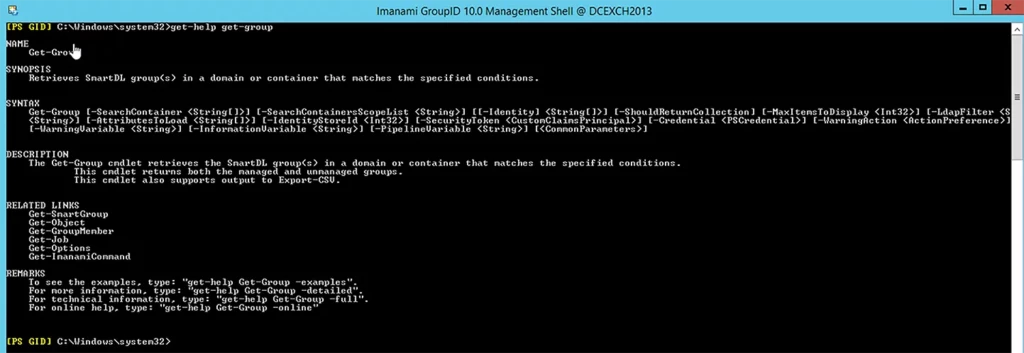
Netwrix GroupID also provides a management shell based on PowerShell technology for more advanced tasks. It offers a cmdlet similar to Get-ADGroup, which is called Get-Group. This cmdlet can perform almost all the tasks that Get-ADGroup does. Below is a description of the Get-Group command:
Conclusion
The Get-ADGroup cmdlet enables administrators to search for Active Directory groups in a variety of ways and control the properties that are displayed in the results. If you prefer an easy-to-learn and flexible GUI interface and comprehensive group, user and entitlement management capabilities, we invite you to take a look at Netwrix GroupID.


