Virtual private network (VPN) is extremely valuable technology, especially for organizations with a remote or hybrid workforce. VPN provides users with a secure and encrypted connection so they can access the corporate network over the internet — while keeping your confidential data and sensitive systems safe from prying eyes. VPN can also hide your IP address so that you can visit websites that are not normally accessible from your location.
Organizations can control use of their VPN using Active Directory security groups: You create one or more Active Directory security groups, grant them permissions for VPN access, and then add users to the appropriate groups based on their needs.
However, managing security groups with native tools and manual processes is time-consuming and highly prone to errors that increase the risk of breaches, downtime and compliance violations. Netwrix GroupID simplifies Active Directory VPNmanagement via security groups. This article explains some of the key use cases.
Delegating Control over VPN Usage
It’s essential to ensure that only the appropriate users are members of any security group — especially groups that enable members to use VPN for remote access. IT team members often do not have sufficient information about a user’s responsibilities to make those decisions, resulting in excessive permissions that increase security risks.
Netwrix GroupID provides a feature to help: You can apply a setting that requires a group’s owner to approve any new members. For example, a team member of mine was unable to access the VPN on our network. I was able to quickly understand the cause of the problem: He was not a member of the required security group, “Access from home.” Using the Netwrix GroupID workflow, he sent the group owner a request to join the group. As soon as it was approved, his VPN connection issue was resolved.
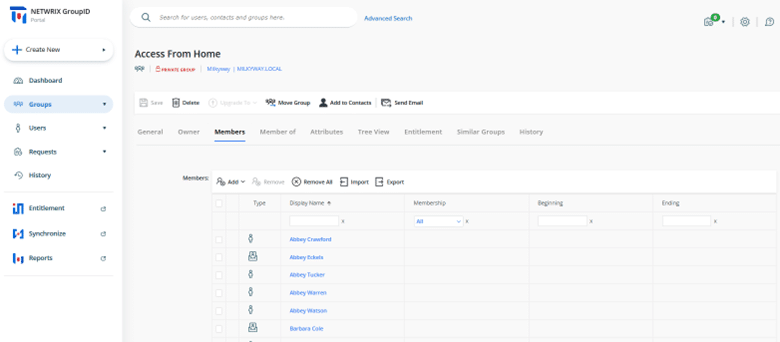
Enabling Users to Request VPN Rights for Themselves or Others
Netwrix GroupID also enables you to control who can request changes to group membership, including joining or leaving a group that grants VPN access. You can allow any or all of the following:
- Any user can place a request to join or leave a group.
- A manager can place a request to join or leave a group on behalf of their direct reports.
- Users can place a request to join or leave a group on behalf of their peers (a peer is a user who reports to the same manager).
Granting VPN Access for a Specified Time Period
While users who regularly work from home need permanent access to VPN, others might need it only for a certain time period, such as a particular month when they are authorized to work remotely.
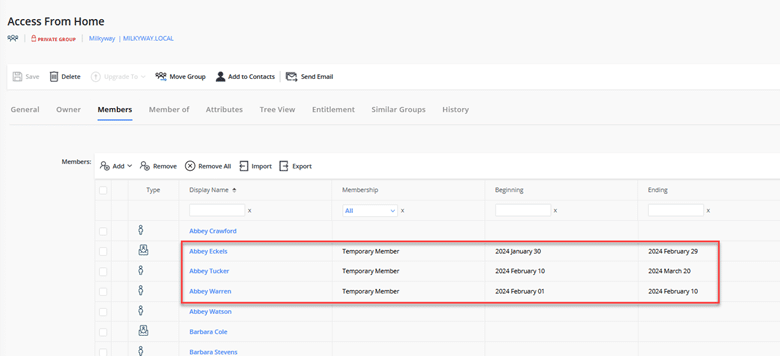
Granting Temporary VPN Access to One User
Netwrix GroupID makes it easy to grant a user temporary membership in the appropriate security group: The group owner simply specifies the date when the user’s membership should begin and the date when it should end. The solution automatically modifies the group’s membership appropriately.
Business users can explicitly request temporary membership when requesting to join a group. They can specify a custom date range or simply choose one of the pre-defined values that shows in the list, such as 7 days, 30 days or 90 days.
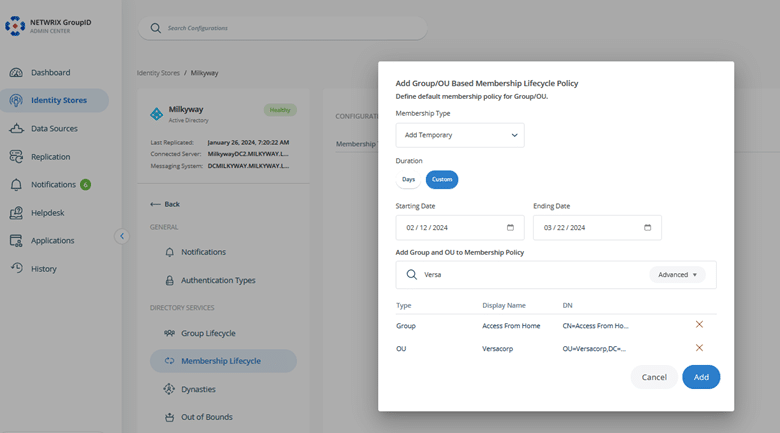
Granting Temporary VPN Access to a Group of Users
You can also set up a policy that grants multiple people VPN access for a designated period. For example, you can give VPN access to the Engineering team for one month and to the HR team for two months.
Conclusion
Effectively management of your Active Directory groups is essential to controlling VPN access to your network. Netwrix GroupID streamlines and automates a wide range of group management tasks, including keeping VPN access rights under control to minimize risk. Moreover, it seamlessly integrates with Entra (formerly Azure), Microsoft 365 and Google Workspace for comprehensive identity and access management.
FAQ
Is Active Directory (AD) a Virtual Private Network (VPN)?
No. Microsoft Active Directory is a directory service for managing and organizing network resources, such as users and computers, in a Windows environment. VPN is technology that creates a secure and encrypted connection over the internet so users can securely access a private network from a remote location.
How do I set up a VPN in Active Directory?
Setting up a VPN in Active Directory involves the following tasks:
- Create one or more Active Directory security groups, being sure to label them with descriptive names.
- Grant VPN access permissions to each group.
- Add users to the appropriate security groups based on their VPN access needs and classification.
- Deploy and configure a VPN solution, and integrate it with Active Directory for user authentication.
Can I join an AD domain over a VPN?
Yes, when you connect remotely via VPN, your computer can establish a secure connection to the domain controller, allowing you to join the domain as if you were physically present on the local network. Note that the necessary VPN and domain-joining configurations must be in place.
How can I access Active Directory remotely?
First, ensure that proper security protocols and permissions are in place. Then follow these steps to access Active Directory remotely:
- Establish a secure VPN connection to the network where Active Directory is hosted.
- Use remote desktop tools to connect to a server or other computer in the network.
- Use Remote Server Administration Tools (RSAT) or another tool to access and manage AD resources.


