Get-ADComputer Cmdlet
The Get-ADComputer cmdlet retrieves a single computer or several computers from Active Directory.
Get-ADComputer Cmdlet: Syntax
Syntax 1:
Get-ADComputer -Filter <string> [-AuthType <ADAuthType>] [-Credential <pscredential>] [-Properties <string[]>] [-ResultPageSize <int>] [-ResultSetSize <int>] [-
SearchBase <string>] [-SearchScope <ADSearchScope>] [-Server <string>] [<CommonParameters>]
Syntax 2:
Get-ADComputer [-Identity] <ADComputer> [-AuthType <ADAuthType>] [-Credential <pscredential>] [-Partition <string>] [-Properties <string[]>] [-Server <string>]
[<CommonParameters>]
Syntax 3:
Get-ADComputer -LDAPFilter <string> [-AuthType <ADAuthType>] [-Credential <pscredential>] [-Properties <string[]>] [-ResultPageSize <int>] [-ResultSetSize <int>
] [-SearchBase <string>] [-SearchScope <ADSearchScope>] [-Server <string>] [<CommonParameters>]
Get-ADComputer Cmdlet: Key Parameters
The following are the key parameter of the Get-ADComputer cmdlet:
- Identity
- Filter and LDAPFilter
- Properties
- SearchBase
- SearchScope
Note that you must use either the Identity parameter, or the Filter or LDAPFilter parameter.
Identity
Use this parameter to specify a particular Active Directory computer to retrieve. If two or more matching objects are found, the command will return a non-terminating error.
The Identity parameter accept values in the form of:
- GUID
- Distinguished Name (DN)
- samAccountName
- SID
Alternatively, you can provide a computer object through the pipeline, or use a computer object variable, such as $Computerobject.
For instance, if your computer is called GroupID10Corp, you would use this command:
Get-ADComputer -Identity GroupID10Corp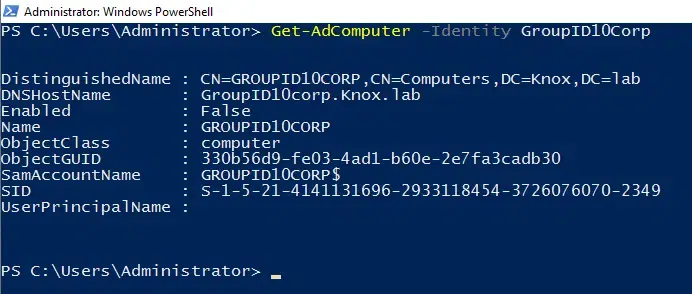
If a distinguished name is used as the identifier, then it is used to compute the partition to be searched. If an identifier other than the distinguished name is used, the cmdlet uses the default context, which is mostly the connected domain of the logged-on user or the user performing the search.
Filter and LDAPFilter
To retrieve multiple computer objects, use either the Filter parameter or the LDAPFilter parameter:
- With the Filter option, you can write query strings for Active Directory using the PowerShell Expression Language. Value types obtained by the Filter parameter are supported for rich type conversion in the PowerShell Expression Language syntax.
- The LDAPFilter parameter can be used if your LDAP query strings already exist.
Filter
Use the Filter parameter to find multiple computer accounts based on the criteria you specify. For example, to locate all computers whose names begin with the string GID, use this command:
Get-ADComputer -Filter "Name -like 'GID*'"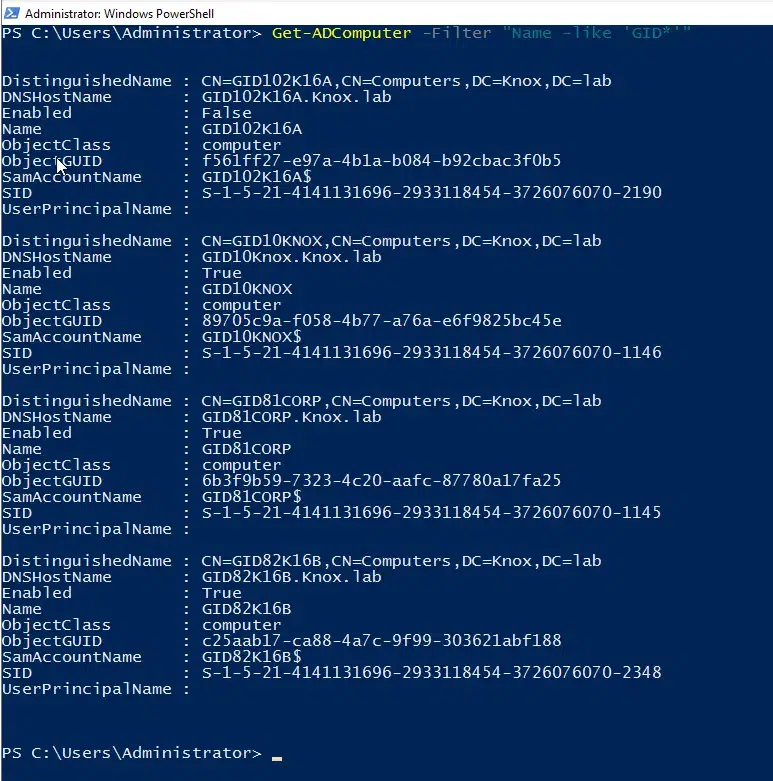
To retrieve all computer accounts in the directory, use the wildcard (*) character, as shown here:
Get-ADComputer -Filter *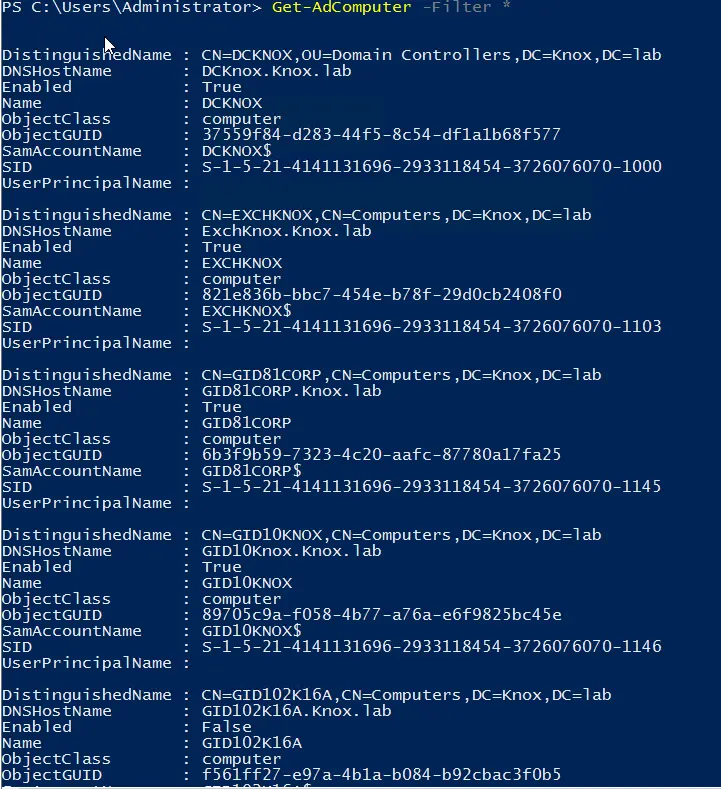
LDAPFilter
If you are skilled with LDAP, you can use the LDAPFilter parameter to zero in on the precise computer you’re looking for. For example, this command will locate all computers that begin with the letter Q:
Get-ADComputer -LDAPFilter "(name=Q*)"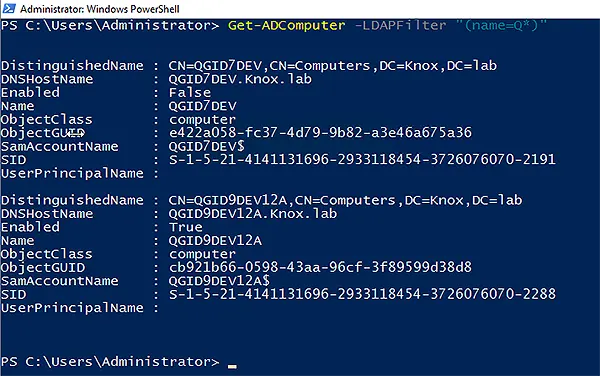
Properties
By default, the Get-ADComputer cmdlet retrieves each computer’s name and distinguished name. While computer objects do not have as many helpful properties as user and group objects, there are additional properties that can be useful, such as:
- BadLogonCount
- BadPwdCount
- IPv4Address
- Enabled
- LastLogOff
- LastLogonDate
- LogonCount
- OperatingSystem
- OperatingSystemVersion
- WhenCreated
Use the Properties parameter to obtain these properties, as shown here:
Get-ADComputer -identity EXCHKNOX -Properties LastLogonDate,IPv4Address,OperatingSystemVersion,OperatingSystem,WhenCreated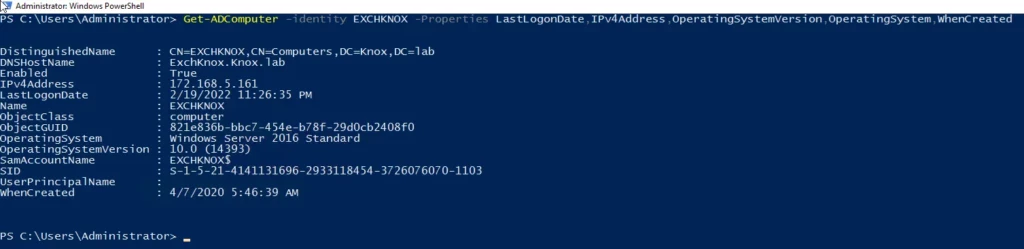
SearchBase
Use the SearchBase parameter to restrict the search to just one OU. For instance, if you want to see all your DCs, you might limit your search to the Domain Controllers OU.
The distinguished name (DN) of an OU must be specified in the SearchBase parameter. Here is an example of how to find every computer account in the computers OU in the Knox.lab domain:
Get-ADComputer -Filter * -SearchBase "CN=computers,DC=knox,DC=lab"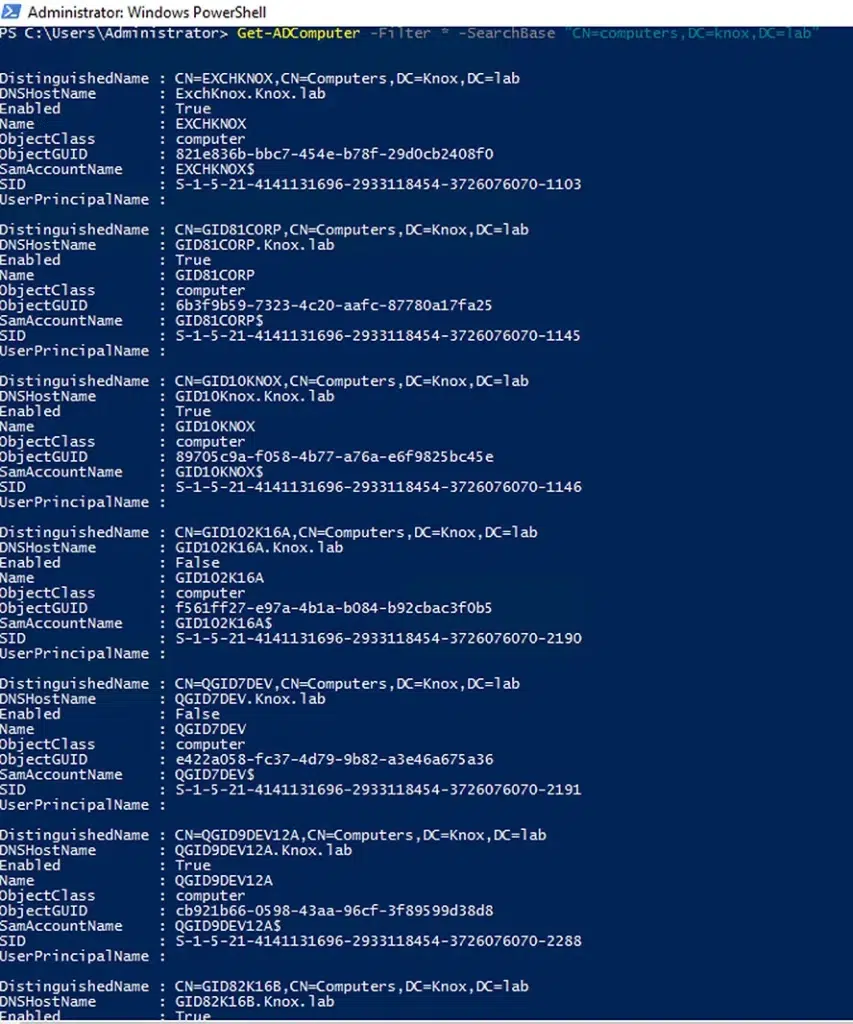
SearchScope
With the SearchBase parameter, PowerShell returns computer accounts from only the specified OU, and not those in any child OUs. Use the SearchScope parameter to control how deep the search should go:
- 0 or Base — Returns only computers in the base OU
- 1 or OneLevel — Returns computers in the base OU and its immediate child OUs
- 2 or Subtree — Returns computers in the base OU and all sub-OUs
For example, the following cmdlet will search for computers only in the base OU specified:
Get-ADComputer -Filter * -SearchBase " OU=Computers OU,DC=Knox,DC=lab" -SearchScope OneLevel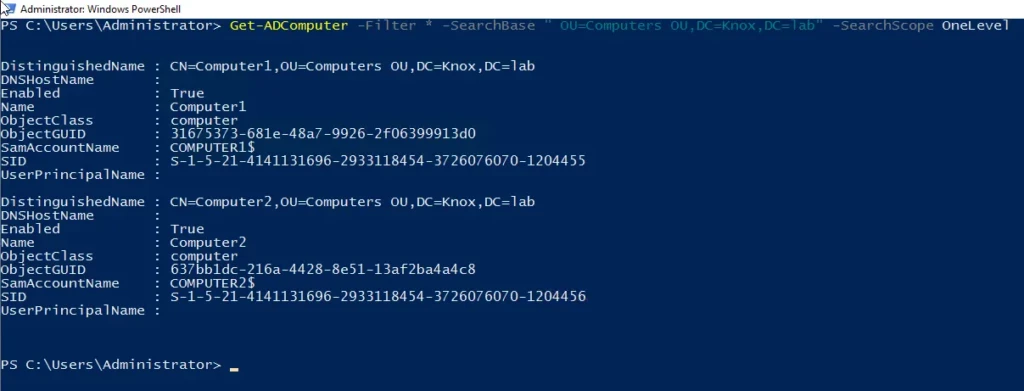
And the following cmdlet will look for the computer objects in the base OU and all its child OUs:
Get-ADComputer -Filter * -SearchBase " OU=Computers OU,DC=Knox,DC=lab" -SearchScope SubTree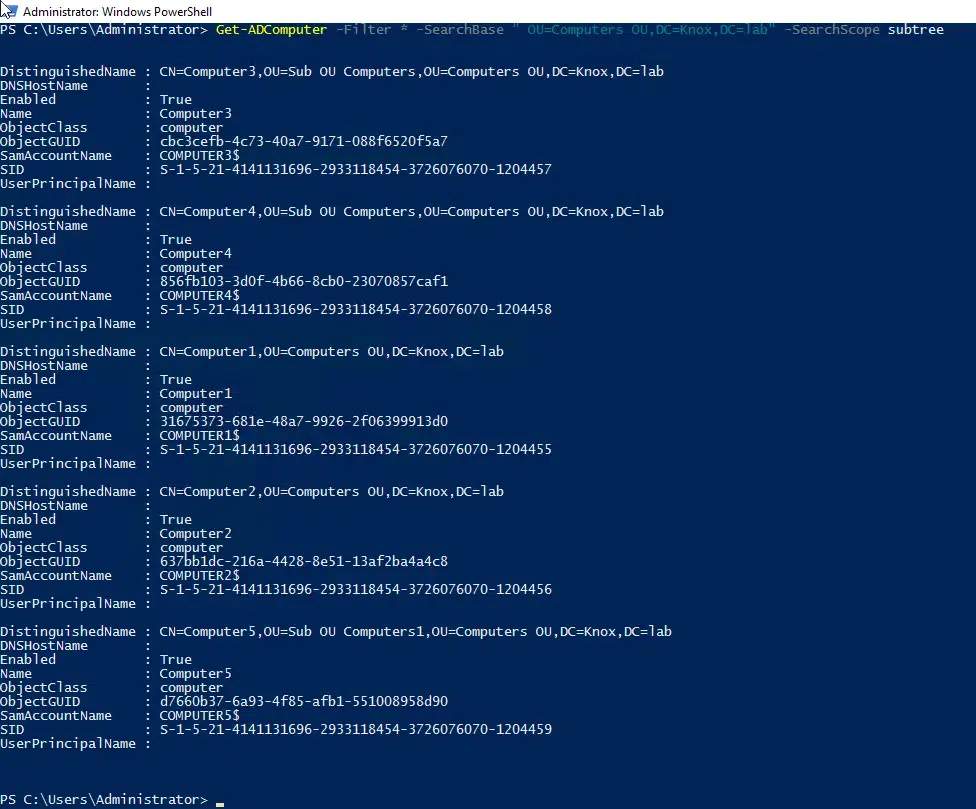
Get-ADComputer Cmdlet: Examples
Let’s look at some examples for using the Get-ADComputer cmdlet:
- Get Computer Objects Based on Operating System
- Get All Inactive Computers
- Get All Disabled or Enabled Computers in Active Directory
- Export the Results to CSV
- Export Specific Properties to CSV
- Export Enabled and Disabled Computers to CSV
Get Computer Objects Based on Operating System
System administrators frequently need to find all computers with a given operating system (OS) version in order to upgrade the OS or apply a policy.
The following cmdlet retrieves the name and OS of all Active Directory computers:
Get-ADComputer -filter * -Properties * | Select Name, OperatingSystem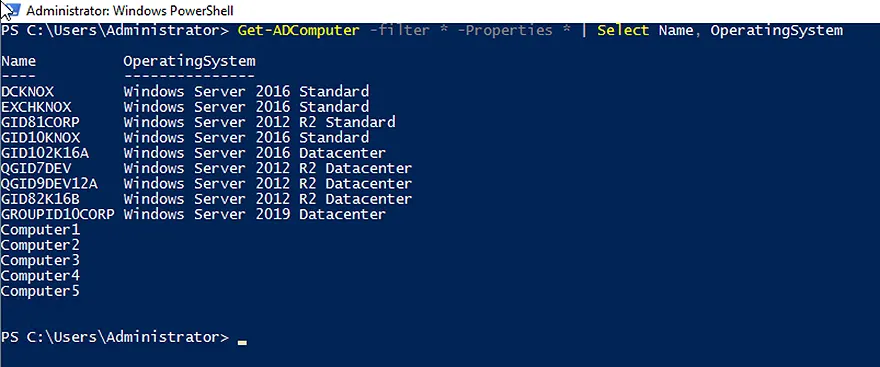
To list all computers with a specific operating system, use the following command:
Get-ADComputer -Filter {OperatingSystem -like '*Windows Server 2016*'}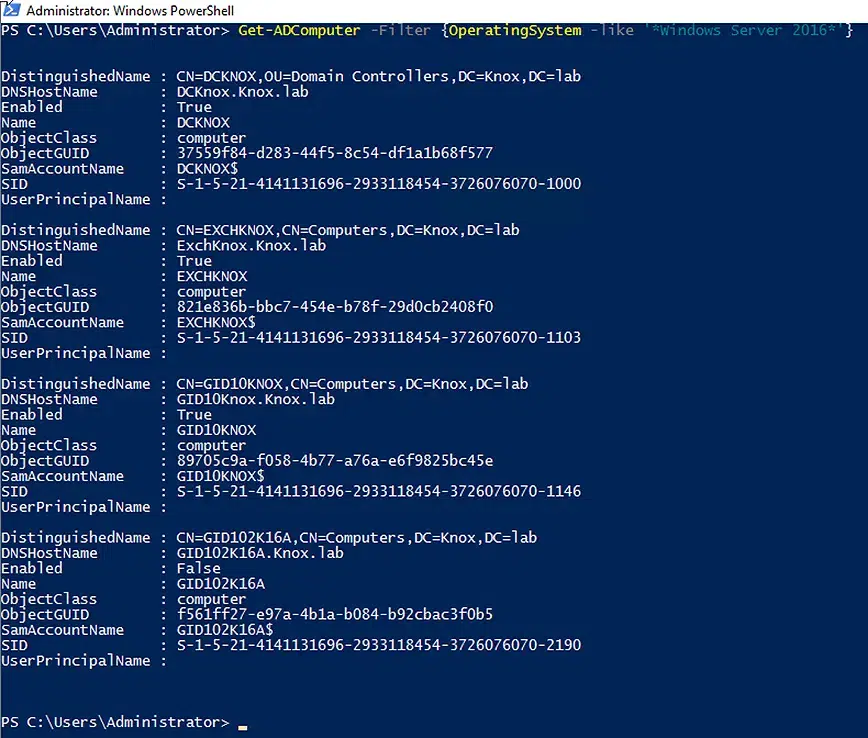
The above script filters the computer objects by the Windows Server 2016 OS.
To obtain information on the operating systems of computer objects residing in a specific OU, use the command below. Get-ADComputer retrieves the computer accounts in a particular OU, including their OS. It passes the output to the second command, which formats the information into a table and sorts it by computer name.
Get-ADComputer -filter * -SearchBase "CN=Computers,DC=Knox,DC=lab" -Properties OperatingSystem | Sort Name | Format-Table Name,Enabled,OperatingSystem -AutoSize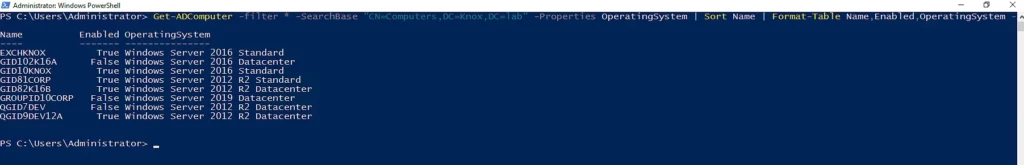
To export the results of a cmdlet, use the Export-CSV cmdlet with the location where you want to save the output, as shown below:
Get-ADComputer -filter * -Properties * | Select Name, OperatingSystem | Export-CSV C:\Computers.csv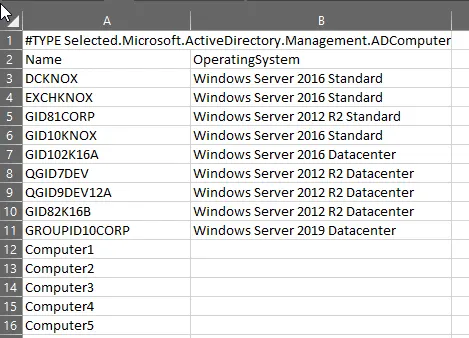
Get All Inactive Computers via Get-ADComputer
Do you need to know how many of your computers are not being used? The script below will find all computers that have been idle for more than 90 days. First, we create a date variable by taking the current date and deducting 90 days. Then we filter the Get-ADComputer cmdlet based on lastlogondate. The last line is an alternate version of the cmdlet that provides more readable output.
$DesiredDate = (Get-Date) – (New-TimeSpan -Days 90)
Get-ADComputer -Filter ‘lastlogondate -lt $DesiredDate’ | ft
# Choose the canonicalName,lastlogondate and name for computers as a list.
Get-ADcomputer -Filter 'lastLogondate -lt $Desireddate' -properties lastlogondate, canonicalName | select lastlogondate,name,canonicalname | ft –AutoSize
Get All Disabled or Enabled Computers in Active Directory
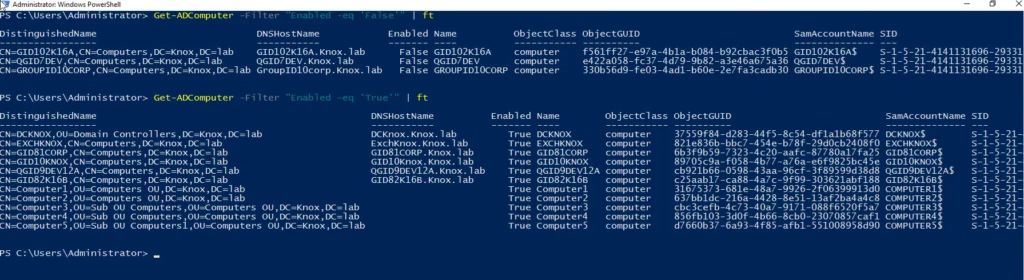
To get a list of all the disabled or enabled computers in Active Directory, use the following cmdlets, respectively:
Get-ADComputer -Filter "Enabled -eq 'False'" | ft
Get-ADComputer -Filter "Enabled -eq 'True'" | ft
Export the Results to CSV
PowerShell results can easily be exported to a CSV file for further analysis or reporting.
Use the following command to export every AD computer object to a CSV file:
Get-ADComputer -filter * | Export-CSV c:\computersdetail.csv -NoTypeInformation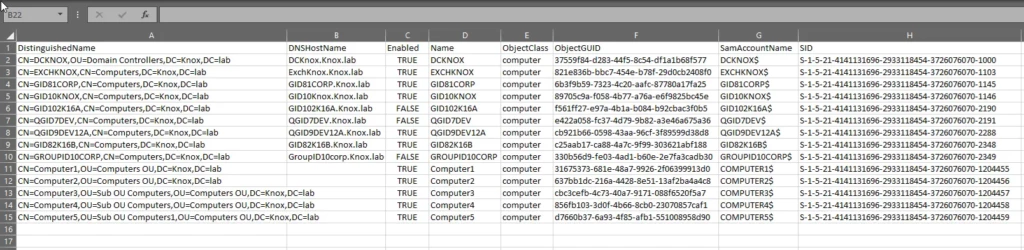
Export Specific Properties to CSV
When you use the Filter parameter with the wildcard character as shown above, only a couple of properties are retrieved. The following command will retrieve a specific set of properties and export the result to a CSV file for further analysis:
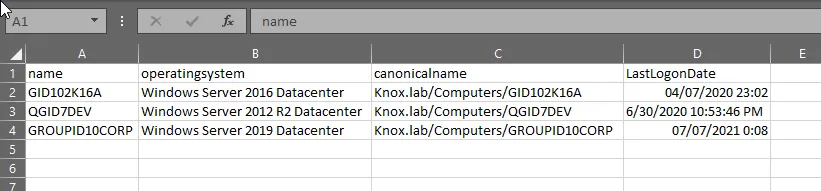
Get-ADComputer -filter * -properties operatingsystem,LastLogonDate,canonicalname | select name,canonicalname,operatingsystem,LastLogonDate | Export-CSV c:\computers.csv -NoTypeInformation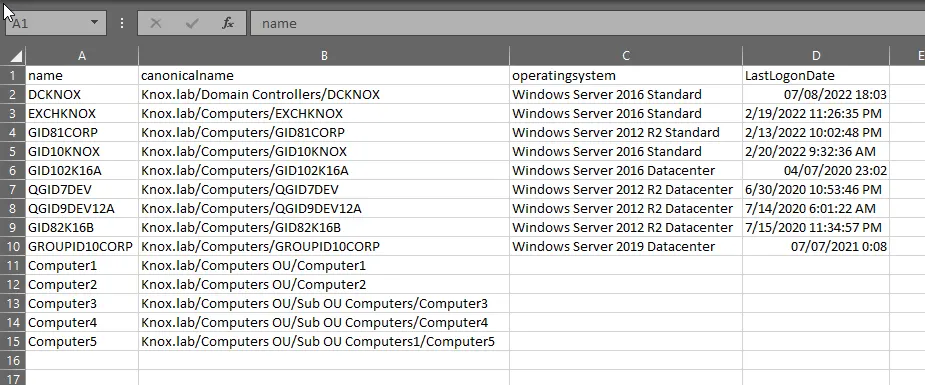
Export Enabled and Disabled Computers to CSV
Earlier, we used filters to search for enabled and disabled computers. Here is how to use the same filters and export the resulting list to a CSV file.
Export Enabled Computers
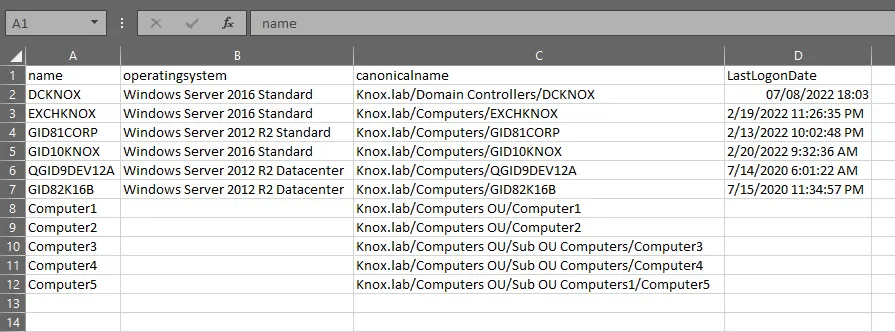
Get-ADComputer -filter "Enabled -eq 'true'" -properties operatingsystem,canonicalname,LastLogonDate | select name,operatingsystem,canonicalname,LastLogonDate | Export-CSV c:\computers.csv -NoTypeInformationFollowing are the results for all enabled computers in Active Directory:
Export Disabled Computers
Get-ADComputer -filter "Enabled -eq 'false'" -properties operatingsystem,canonicalname,LastLogonDate | select name,operatingsystem,canonicalname,LastLogonDate | Export-CSV c:\computers.csv -NoTypeInformationIf you look closely at the LastLogonDate column, you will see the date when each computer was last used for login.
Summary
The Get-ADComputer cmdlet is a great way to retrieve information about one or more computers. For instance, you can quickly list all computer objects with a particular operating system to facilitate security updates or end-of-life deprovisioning, or discover all inactive or disabled computers to inform your Active Directory cleanup process.This can be best achieved by Netwrix GroupID.


