Identity management has been defined by wikipedia (great source, I know, but bear with me) as:
Identity management … is a broad administrative area that deals with identifying individuals in a system (such as a country, a network or an organization) and controlling the access to the resources in that system by placing restrictions on the established identities.
And that’s where identity and access management (IAM) seems to live, managing individuals or users. Provision/deprovision the user. Add a role to the user. Give this user access to this or that resource.
 The problem is there are a lot of users. Applying permissions to each user is unwieldy and an overwhelmingly expensive task. Roles try to solve that. In a role-based identity world, User A and User B are both salespeople in the New Orleans branch so they get the permissions that a New Orleans sales rep should have. But then again, not every employee needs the same things and including/excluding users from certain roles and keeping track of that is again a very overwhelming and expensive task.
The problem is there are a lot of users. Applying permissions to each user is unwieldy and an overwhelmingly expensive task. Roles try to solve that. In a role-based identity world, User A and User B are both salespeople in the New Orleans branch so they get the permissions that a New Orleans sales rep should have. But then again, not every employee needs the same things and including/excluding users from certain roles and keeping track of that is again a very overwhelming and expensive task.
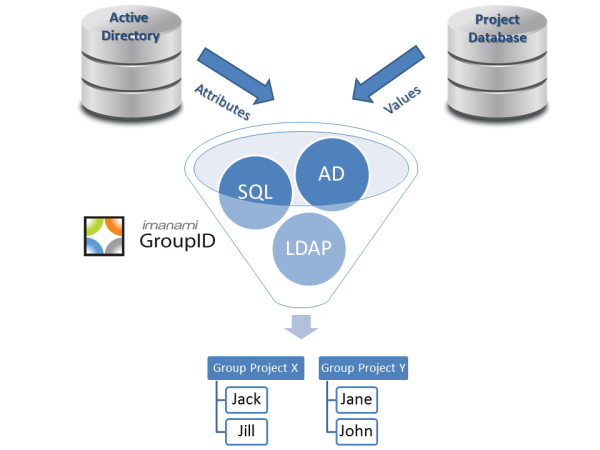
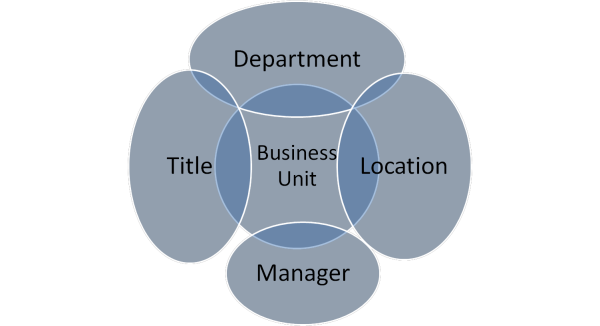
That’s where groupcentric identity management can come into play. Most organizations already have the Active Directory group structure in place. You use it for domain admins, SharePoint admins, Exchange admins, and of course Exchange distribution lists. But if you think of each unique user as belonging to a variety of groups such as department, location, title, project teams, etc, it become simple to create Active Directory groups that have the requisite permissions and add users to the groups that fit.
If you have a strong group management process in place, you can manage permissions in a more flexible manner than roles or user-centric identity management ever could. Just put users into the appropriate groups based on what you know about them from AD, HRIS, and/or that spreadsheet that the CIO’s assistant keeps and give permissions to those groups.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.