The Role of Roles in Delegating Access
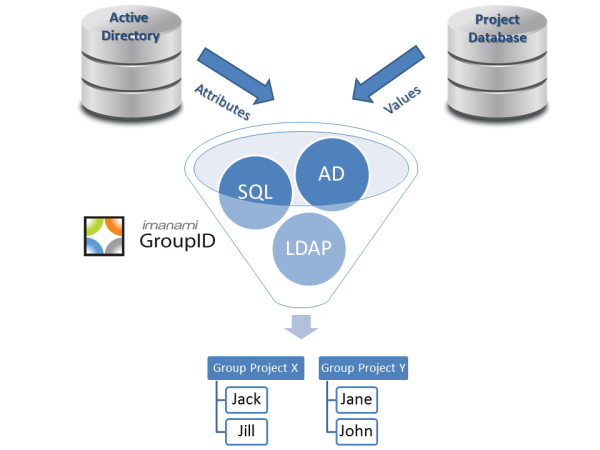
The delegation of directory administration to those outside of IT is a concept whose time has come. But it can’t be done hap-hazardly; IT needs to define what is being delegated and to whom. We’re at a point in the evolution of our industry that two truths have come to fruition: IT no longer has…