There is a long continuing debate on using SharePoint groups or Active Directory groups for SharePoint site access. Based on our own poll (in the nav bar to the right) and the one on SharePointEdu Tech, approximately 85-90% of admins use either Active Directory groups exclusively or partially for granting access.
My guess as to why? Because IT controls Active Directory and SharePoint. And IT knows Active Directory groups. One commenter over at SharePointEdu Tech points out that from a business user’s perspective, Active Directory groups stink (I am paraphrasing). And this is true for most companies that don’t have a handle on Active Directory group management.
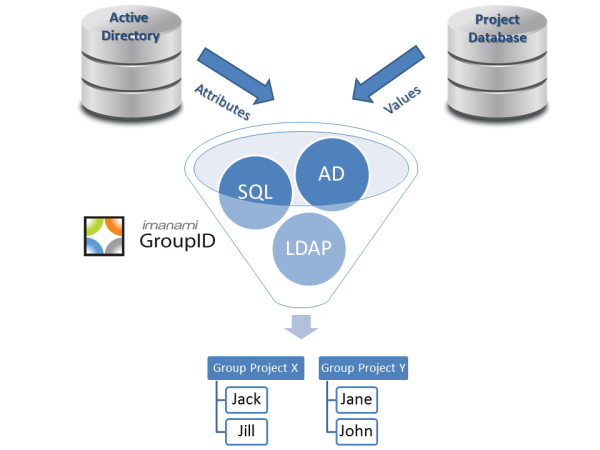
Luckily, there are third party tools available to help IT keep the business users happy (as pointed out by a commenter near the end of the thread). Imanami’s GroupID is a great example of one of those tools. Since our expertise is Active Directory group management, it makes sense for us to share some best practices.
- Create Dynamic Active Directory Security Groups for those broad brushed groups. Anything that can be defined by a query against either Active Directory or any other data source. This eliminates the business user’s complaint that a group isn’t up to date. Active Directory usually knows your department, location, title, et cetera; query those attributes and as soon as it is updated, your group’s membership will automatically reflect it.
- Empower End-Users to Manage their Own Groups through Active Directory self service. Seriously, who knows who should have access more than the business owner? Give them the ability to add/remove members. Put workflow restrictions if you have to, but most likely you can trust the person managing the group & SharePoint site.
- Allow End Users to Request Membership in Active Directory Groups. This is trickier, you have to have the correct workflows in place or things can get out of control. Some groups should allow anyone in (the book club for example); some should require the approval of the group owner (new product team); while some should never allow an opt-in (the earnings committee).
- Restrict Nested Groups when offering self service. Want to get your permissions (not just to SharePoint but to anything) tied up in a big knot? Allow nested groups without some sort of IT oversight.
- Require Group Descriptions. Always. Nobody will ever be able to decipher what SG-OntBkClb means. At least make the group owner try to define it.
- Expire Un-Necessary Groups. Don’t delete them but make group owners periodically renew the groups if they want to keep them. Token bloat is not fun and being a member of SG-OntBKClb so that you have access to the list of recommended books from the Ontario Book Club that is never updated doesn’t help the business. Expire it and make the group owner renew it if it still has some value.
Following these tips should save both IT and the business time in managing SharePoint access. My mantra is always “Automate, then delegate, then help desk call“. Since there are very valid reasons to use Active Directory groups instead of SharePoint groups, it is essential that the business have tools to manage their own groups without running afoul of corporate standards. And those groups that IT controls should be trustworthy to the business.
Take a look at GroupID to see how all of this will work to help the business and IT work together to grant SharePoint access efficiently and accurately.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.