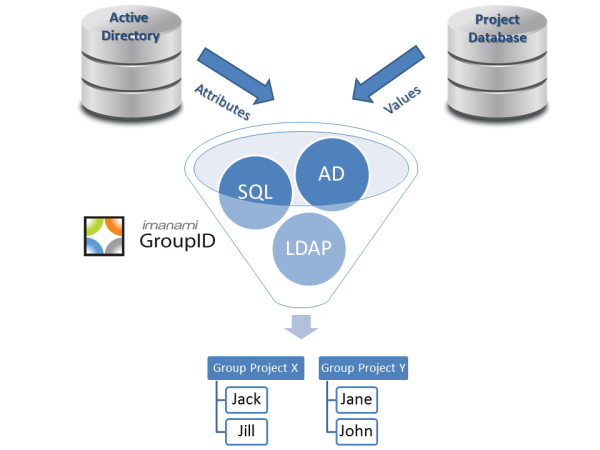
Everybody knows you have to get users in Active Directory. With the incredible market share that Active Directory has, it’s just the first step to doing anything for the vast majority of organizations. When an employee starts, you want that employee as a user in Active Directory immediately so they can start working.
Incredibly, this basic tenet of Identity and Access Management (IAM) is taken for granted quite often. Our own research shows that over 50% of organizations just live with the status quo and don’t do anything to ensure that this provisioning process is automated. It seems so basic that I rarely write about it and take it for granted that a prospect is doing it when talking about more advanced IAM concepts.
The advantages are obvious. A new employee needs a network account to do anything these days. They cannot even get to their email or open Excel without logging into a computer with their Active Directory account. Just as important is deprovisioning a user when they leave…you don’t want them checking email or opening Excel today if you fired them yesterday.
One of our sales guys followed up on a lead a few weeks ago after having exchanged emails with a guy using his corporate email address. The contact had only listed the company’s main number but our guy called it to talk over a concept. The receptionist informed him that the person he was calling had left the company 3 months prior! Yet he still had access to his corporate email account. That is a candidate for a provisioning/deprovisioning solution if I ever saw one!
So, don’t ignore the basics. Make sure you can provision users into Active Directory, get them email and network access first. For an easy way to do this, check out GroupID Synchronize, we can have this provisioning and deprovisioning system in place in just a few hours.
Remember, automation is key, don’t fall prey to the age old build it yourself Rube Goldberg machine trap:
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.