How is your Active Directory (AD) being managed? Do you have any orphaned groups (groups without owners)? Are there groups that have outlived their purpose? Do you have users that are members of groups and they no longer need to be part of these groups? An ongoing attestation of groups is key to answering these questions.
Group objects in your directories tend to fall into a state of disarray without proper oversight. This problem becomes multiplied if you have multiple on-prem and cloud-based directories, making it even more necessary to keep groups properly configured.
Fully understanding and evaluating your current AD situation is key. Fix it before it becomes unfixable!
What is Group Attestation?
Group attestation describes the process where individual reviews and certifies that specific aspects of a group object’s configuration are correct and current.
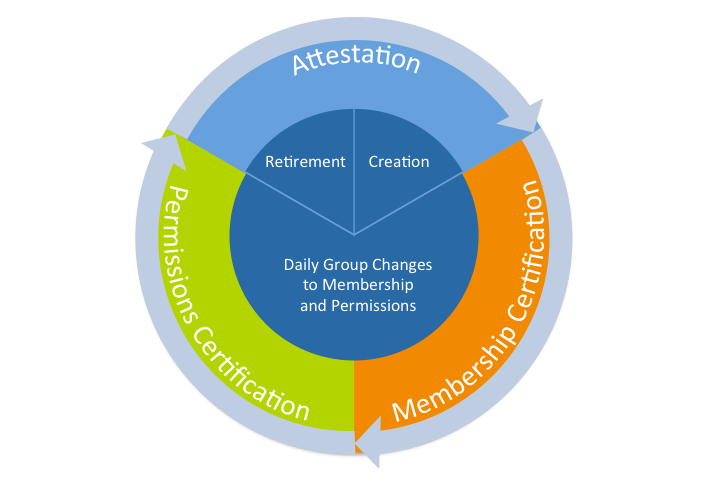
Let’s begin the discussion of group attestation by level-setting what exactly needs to be attested to. There are three key areas of a group object that require frequent attestation:
- Group Membership – Users and/or nested groups as members are validated. This means they represent the current set of users utilizing the group’s assigned permissions.
- Group Permissions – Permissions assigned are validated. These only the ones needed for group members to accomplish their work-related tasks.
- Group Existence – The group’s necessity to the business is validated. Groups with no current purpose should be deleted or disabled (if possible).
Here is an Example
A healthcare institution has a security group granting access to Patient Records; 324 out of 2,000 employees at the institution have access to it. And, once a quarter, a group admin or owner looks at the membership and says, ‘it is good to go’.
Does the admin really know anything about those 324 group members? Does the admin know if one employee is missing or one more should be added? The answer is ‘NO’ because more information is required on those users. Most of all, data accuracy needs to be addressed.
- What if the admin knew that all the users were in the administration department? That would help.
- What if admin knew that 3 new users were added this quarter and 5 were removed? That would make the attestation much easier and ensure that the admin looked at it.
Learn more: Healthcare Active Directory Management
Who is Responsible for Group Attestation?
Think about the above across the context of all your directories existing both on-prem and in the cloud. Group attestation requires some dedicated (while not significant) time for every group you have within the overarching directory environment. Add it up, and this begins to sound like a lot of work.
Read more: 4 Reasons for Managing Groups and Identities in a Hybrid World
So, who’s responsible to do the work of attestation?
The initial response from the C-suite may be that IT needs to do it. But it’s not that simple. IT isn’t always the best option; there are actually two very good answers to the question:
- IT – Even though IT is overburdened, they are the right choice when it comes to groups providing the highest of elevated permissions. Administrator-type groups, and any groups that provide access to entire applications, platforms, virtual environments, etc., should be attested to by IT.
- Users – IT isn’t always current on exactly how a group is being used. In many cases, a user closer to the daily usage of a group is a better choice. Details like who should be a member, and whether permissions meet (or even exceed) those needed for users to be productive may be more accurate with a user performing the attestation. To be clear, you don’t want just any user in charge of attestation; think the line of business owners, a department head, etc.
There are likely far more groups in your organization than IT personnel. So, an added benefit of having a user perform the attestation is that each group can have a different user associated as its owner.
How should Group Attestation be done?
At the end of the day, the most important thing is that the right individual within the organization frequently attests that a group is correctly configured.
There are a few ways to accomplish group attestation:
- A mix of manual Work, Policy, and Process
Defining a group’s owner is the first step. Then policy dictates a procedure be followed when assigning permissions to a group that involves the owner for approval. The same goes for membership changes. While all done pretty much manually, the idea is to always keep the owner in the loop.
- Use Automated Workflows
Using a Group Lifecycle Management solution simplifies this process dramatically. Membership changes done via such a solution can include the need for approval from the owner in the workflow. Owners can be sent an automated reminder email and can attest a group’s necessity at a regular frequency.
Permissions are the only aspect of attestation that can’t easily be automated. No permission data is stored as part of the group object itself; it’s normally located within one or more external applications, platforms, and systems.
- Making Group Attestation work
It’s a relatively simple matter, really. Determine and assign an owner for each group. Then, establish the processes by which that owner is kept abreast of any changes to the group or its use. Lastly, provide a way for the owner to easily attest to a group’s configuration and necessity.
Take one step at a time
The challenge in applying this to your environment will be found in how you accomplish this. The use of third-party solutions streamlines the process, making it a simple and efficient process, but some organizations still leverage native management tools to get the job done.
In either case, the important thing is to have something in place. Some attestation is certainly better than no attestation at all. Start the process of building out how your organization can and will begin group attestation, setting the required frequency. As your thinking around group attestation matures, so will your process, and use of tools to complete the work.
What’s Next?
To help you get started, I recommend you try the free Active Directory Health Meter service from Imanami. There is no obligation, and it will give you some insights as to your relative health and give you some simple suggestions based on industry best practices. Go here to get started.
Enforce Group Attestation with GroupID
GroupID is the leading Active Directory Group Management solution that helps organizations in delegating, automating, and managing resources that span more than one domain.
The demands of every organization are unique. What’s not unique are the pressures on IT to make sure people have the right access to secure resources and systems. That’s where we fit in! We offer solutions for different use cases across multiple verticals. Using GroupID solutions, you can enforce and automate regular attestation of your group, without a hassle.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.