What is a Enterprise Hybrid Cloud?
Enterprise Hybrid Cloud can have everything in cloud among the services, like Okta, Sail Point, ServiceNow, Active Directory & Azure AD taking to each other.
For example, a Helpdesk Request can generate from Service Now for a new user onboarding that requires provisioning an account in Okta for Single-Sign On and Authentication to external apps allowed by organization. Same request can be sent to Active Directory / Azure AD to provision a new user account and assign group memberships that are important to meet business needs
In a nutshell, it involves orchestration among services by consuming events from other Services (service can be an App, Platform, SaaS etc.)
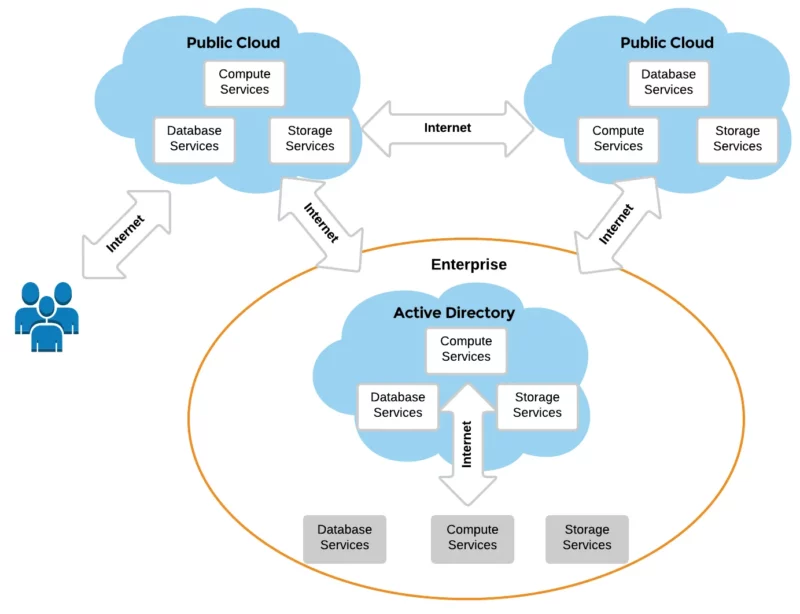
Enterprise Hybrid Cloud: An Organizational Choice
Running some part of your business in a cloud, is a choice every organization faces. The ability to easily extend your environment by including cloud applications without the headache of maintenance itself makes financial and operational sense. Yet, there are risks you should know about.
As organizations shift to cloud-based applications, there remains a partial reliance on their on-premises identity store, thus, the enterprise hybrid cloud takes form.
In this article, we will discuss why it is imperative to continually manage active directory ,azure ad groups and identities across your enterprise hybrid cloud. It also provides ways to simplify this work.
Hybrid Environment: Different Day, Same Attack Vectors
In a survey by Statista in 2021, over 88 percent of cloud Identity and Access Management (IAM) respondents stated that they had the problem of unused credentials. Instead of removing or disabling the credentials once they are unneeded, companies ignore them. This approach creates hacking opportunities, including ransomware threats. While companies resolve their issues of flexibility and lower costs using the enterprise hybrid cloud , they are perilously overlooking that the cloud network still requires maintenance.
Whether your strategy is to use a enterprise hybrid cloud for a transient or a perpetual period, you will still require the means to ensure appropriate active directory and azure ad group security across the entire environment. Digging further down into, what hybrid is as well as the tools available, will continue to evolve and change. This makes creating a plan longer than three years difficult. Hackers aren’t standing still and neither can you.
Active Directory Groups in a Enterprise Hybrid Cloud
There are two specific use cases of groups that require recurring attention in active directories, as well as in cloud directories:
Security
– All assignments of active directory and azure ad permissions and privileges are accomplished directly or indirectly using either a user object or a group account in a directory service.
Productivity
– The details of user or group accounts are needed for email, messaging, and collaboration. If information such as title, location, phone number, email address, etc., is not maintained appropriately, it can have repercussions that may impact user productivity.
Managing groups and identities requires addressing both use cases through proper attestation. User attestation is a process whereby users are responsible for ensuring the accuracy of details and permissions of certain accounts. This process can be performed in several ways. One way is a “Self-service tool” which helps users validate their credentials
Read more: The Value of a Self-Service Portal
However, ensuring the accuracy of active directory and azure ad permissions assigned to groups usually involves a defined process where department heads, line of business owners, and power users are accountable for the pertinence of details, permissions, and group memberships. These people are also called the “owners” of groups.
Following are some major concerns that will make you understand why you need to go through the hassle of managing your groups and identities.
-
Gain Better Control on Data
-
Errors are more common in Enterprise Hybrid Cloud
-
Overcome Security Breaches
-
Compliance Requirement
-
Cost Optimization
Though the scope of Enterprise Hybrid Cloud, may extend beyond Active Directory and Azure AD, we are focusing on Active Directory and Azure AD.
Reason 1: Gain Better Control on Data
For many organizations, groups and identities have only existed within on-premises Active Directory (AD). As organizations keep going through digital transformation, their cloud resources keep on increasing. Given that more than 60% of people responding to a survey stated that management of data on the cloud is extremely challenging, the default assumption should be “if one directory isn’t under control, neither will be the expanded more complex enterprise hybrid cloud environment.”
If Active Directory user and group accounts along with the permissions aren’t regularly validated, how can IT expect to control an ever-growing expanse of cloud applications? The reality is you can’t unless you find tools for it.
Consider the following “Best Practices” to get groups and identities under control with in Active Directory & Azure AD for an enterprise hybrid cloud:
Establish an Employee System of Record
With so many potential “sources” of identities and their details, it’s necessary to have a single source that will eventually be replicated to all applications and directories. Mature organizations that are serious about identity and access management, use their HR platform as it maintains the correct contact details, title, location, manager, etc., and is nearly always up to date.
Get Syncing Right
Different applications and platforms have their attributes and not all user attributes will sync between all your on-prem and cloud-based applications, identity stores, and directories. That’s troubling, right? Having a solution in place that both serves as:
- The initial recipient for the employee system to record data
- The means to sync will help ensure that the entirety of your hybrid environment is using the same group and identity detail.
Reason 2: Errors are More Common in Enterprise Hybrid Cloud
If you employ an enterprise hybrid cloud environment of on-prem active directory and cloud applications, managing data becomes complex. Any single incorrect configuration can propagate throughout the environment. If active group memberships, department assignments, or even job titles are incorrect, there can be an adverse impact on security and productivity, depending on how each cloud resource leverages account attributes within the directory.
Therefore, it’s imperative that you are managing groups and identities in a way that considers the impact, a configuration in your primary identity store will have enterprise-wide, as demonstrated in the “Best Practices” below:
Start the Security Cleanup Now
Even if you’re only using on-premises active directory group management, it needs to be cleaned up now. Cleanup starts with the attestation of every user and group account and group memberships. It’s a lot, but there are tools to help run reports on accounts, as well as to manage accounts that require attention.
Perform Group Membership Attestation
Because a single group can be granted access across every application integrated with your directory, members can access more than they should. Assign owners to groups and have those owners frequently validate the memberships of the groups, anyone not belonging should be removed.
Do Not Overlook Synchronization
If you’re already in an enterprise hybrid cloud environment, the same need for cleanup applies keeping in mind the synchronization and the impact it may have.
Reason 3: Overcome Security Breaches
According to recent research, 60% of all cyberattacks use lateral movement (moving from machine to machine within a network). To accomplish this, attackers need to compromise internal credentials. Attackers attempt to connect to not just on-premises endpoints and servers but to also cloud-based applications and resources. The same is true of phishing campaigns designed to capture cloud applications credentials
Read more: 5 Reasons why Cyberattackers love AD Groups
To avoid security breaches, consider the following “Best Practices”:
Restrict Credential Access to/from the Cloud.
Implementing least privileged access, paying special attention to any ability to cross the hybrid boundary is critical to minimize the threat surface. If users do not require on-premises access, create accounts in the enterprise hybrid cloud (e.g., Okta, SailPoint & Azure AD accounts for M365 access that don’t sync down to your on-premises Active Directory).
Practice Group Permission Attestation.
To truly know you have the least privilege access is implemented, attestation of active directory and azure ad groups is necessary. Initially, this may be a sizable undertaking, requiring application owners to produce permissions reports that may be reviewed.
For every group that exists, it’s important to have a full understanding of what that group has access to. Group owners within directories such as active directory and azure ad should periodically review any permissions assigned to their group for accuracy to ensure only necessary access is granted.
Reason 4: Compliance Requirement
In the last few years, more regulations intent on protecting consumer data have been created by the government that not only contain specifics around what protective measures need to be in place but also come with harsh penalties.
A great example is the California Consumer Privacy Act (CCPA), which is in effect since January of 2020. This law seeks to protect the consumer data of California residents. The law is precise and clear in its wording about constitutes that breach compliance and the related penalties.
These newer regulations such as CCPA, the European Union’s General Data Protection Regulation (GDPR), and many more that are popping up in the United States and around the globe are all serious about the real threat of data breaches and the need for protecting consumer data.
To avoid finding your organization in breach of a regulation protecting data, consider the following “Best Practices”:
Understand Your Compliance Mandates
It’s imperative that you get a full understanding of which mandates your organization is subject to and what the specific data protection requirements are.
Know Where Your Protected Data Resides
You can’t protect what you don’t know about. So, the first step in attempting to be compliant is understanding where protected data exists. This can be on-premises or in the cloud; structured or unstructured. You’ll likely need to utilize a data classification solution to help find all instances of protected data.
Understand Who Has Access
This is a throwback to all the attestation you’ve already done, simply placing the focus on specific data sets that fall under compliance. Ensure only the right people have access to the data through both user and group permissions attestation and group membership attestation.
Reason 5: Cost Optimization
Till now it is evident that switching to hybrid and tracking the cloud inventory is just as essential as on-premises application. Overlooking any of the challenges with the management of enterprise hybrid cloud systems would eventually cost more than it would save. Unattended cloud resources, scattered data, security breaches, and non-compliances are influencing not only in terms of finances but efficiencies as well.
To ensure that you are at the forefront of managing all the aspects of your hybrid set up consider the following “Best Practices”:
Be Proactive
To have better visibility about the consumption of your cloud and on-premise application, you will need a strategy for monitoring the activities. Fortunately, there are some tools that assist in managing proactively across the entire environment.
Use a Strategy that Suits Your Business
You must evaluate and identify the management tools appropriately before you choose them. Most solutions fall short of providing the visibility that your enterprise hybrid environment requires, you must remember that the productivity of your enterprise is non-negotiable.
Enterprise Hybrid Cloud Requires On-going Management
The shift to a modern business, has organizations adopting cloud applications and resources as part of operations. This results in more application-specific directories, permissions being assigned, and users being created. Mix this with IT not addressing the security and productivity issues that will no doubt keep on rising and will lead to IT entropy.
No directory, system, platform, or application has ever become more organized over time with zero effort; as IT extends the logical boundary of the network to include the cloud, it’s necessary to continually and consistently manage the state of groups and identities to ensure organizational security and user productivity.
By considering the reasons outlined in this article and following the best practices offered, your organization’s set of identities and groups will remain in a relatively constant state of being secure and up to date.
While the path is paved with some time dedicated to getting years of mismanagement cleaned up, the work necessary to perform ongoing maintenance of a properly configured hybrid environment can be greatly reduced by leveraging solutions designed to automate the work of managing groups and identities.
Go Next Level for Active Directory Group Management with GroupID
Watch this webcast on Directory Management: When you’re into the Cloud
Imanami is the leader in Group and User Lifecycle Management solutions for active directory. GroupID by Imanami offers a suite of solutions that empowers IT professionals to effectively and automatically provision and manage users and groups. With GroupID, groups and users are always up to date.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.

