The demands of every organization are unique. What’s not unique are the pressures on IT to make sure people have the right access to secure resources and systems. Your unstructured data is a primary target in nearly all worse case scenarios. Protecting such data gets harder if you don’t understand where it exists, who has access to it and how was it granted access. Without that information, structuring a smarter, safer technology environment can be daunting.
The longer a technology platform exists, the more time cyber attackers get for devising ways to exploit the technology. This fits well for Windows–based security. Fortunately, the largely popular operating system and security ecosystem has been robust throughout so the battle for supremacy continues. Complacency, however, still runs rampant and if you are not keeping up, you are the one these cyber criminals are seeking out.
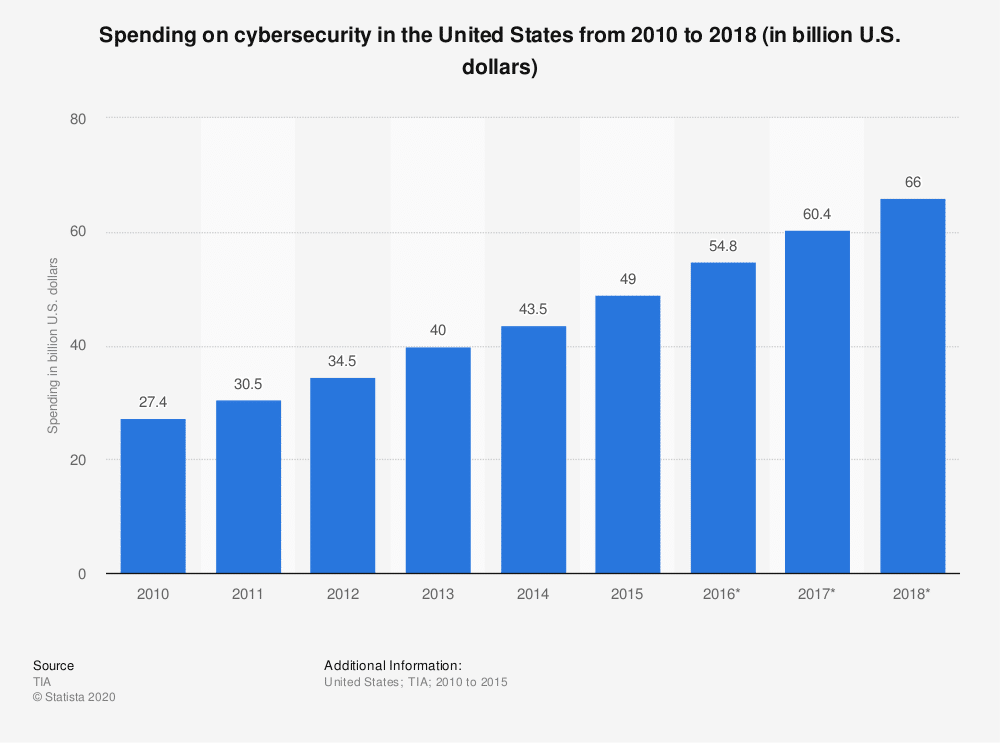
In 2018, spending in the cybersecurity industry reached around 40.8 billion U.S. dollars, with forecasts suggesting that the market will eclipse 43 billion by 2020 as the best-case scenario, taking into account the coronavirus (COVID-19) impact.
How do they do it?
With known vulnerabilities exposed all the time, even amateur hackers are gaining access to vulnerable systems without making much effort. It won’t be shocking if you find yourself with company data held for ransom with no way to combat it.
The means and ways these criminal actors gain access to systems is quite varied. They even leverage multiple vectors to gain illicit access. The most common method of gaining access to your network is sadly, the compromised user account. Once compromised, they will use this account to move around your network with the goal of further penetration. The most likely vector from that point being the Active Directory access and the additional control that can be achieved by leveraging permissions granted to those with entitlements.
Read more: 5 Reasons Why Cyberattackers Love AD Groups
What is Active Directory Entitlement Management?
It enables organizations to manage identity and access lifecycle at scale, by automating access request workflows, access assignments, reviews, and expiration.
Active Directory entitlement management can help you efficiently manage access to groups, and applications. It also helps you with SharePoint Online sites for internal users and also for users outside your organization who need access to those resources.
What happens when you don’t manage it the right way?
If your organization is not reviewing permissions regularly that are given through various entitlements, the risk of a cyber attack increases greatly. As an organization evolves so does its security footprint – making it easy for errors to appear more over time. There are aspects that are frequently overlooked – such as permission assignments providing access to data, applications, services and systems. These may also entail the usual control mechanisms i.e. groups and the membership therein.
With tenure, user accounts will get added to groups, groups will get nested, all of which enables the permission creep to follow those who have had roles added upon or changed. With time, these accounts become increasingly dangerous and act as vehicles for compromising data security. This is especially true for your unstructured data that now most likely consists of at least 80% of your organization’s critical technology assets.
Did you know? As per a survey, respondents stated that the reason their company faced select cybersecurity challenges in 2018 was due to lack of employee education.
Why use Entitlement Management?
Enterprises often face challenges when managing employee access to resources such as:
- Users are not aware about the access they should have, and even with some knowledge, they find it difficult locating the right person for the job i.e. to approve their access.
- Once users find what access they require and then get it for a resource, they tend to keep it longer than required for business purposes.
The above also include users who need access from another organization, such as external users from supply chain organizations or other business partners. For example:
- It’s obvious that no one individual knows all the individuals in other organization’s specific directories and be able to invite them.
- And even if they are equipped to do it, you cannot a person in that organization to remember and manage all the users’ access.
Read more: 3 Steps to Gaining Control and Governance over Permissions
Getting down to the nitty gritty of Entitlement Management
Disregarding the importance of entitlement management enables bad actors to find ways into your environment. Following are some examples:
1) Making changes in Group Membership
When a cyber-criminal gains access to an account with even minimal authority in Active Directory, they will look to change membership in groups that they have access to. Just the simple act of adding an account to another group can greatly increase the compromised account with additional access.
2) Accessing Groups because of Nesting
An elusive way for a hacker to gain access without readily being noticed is through permission inheritance by nesting one group within another.
3) Creating Duplicate Users
With the ability to create another account, a hacker can leave themselves a back door to gain access even if their original compromised account is discovered.
4) Utilizing broad access
Often for simplicity an administrator will grant access to an entire directory or a root level share with sub directories without considering the type of unstructured data contained therein. Bad actors will seek out these types of broadly permissioned shares.
5) Giving way to Permission Creeps
Hackers are astute with how permission creep occurs and seeks out seasoned staff – even those without traditional administrator roles. Why? Because they understand that permissions tend to grow without oversite and management. Tenure alone will expose these tenured accounts as perfect targets for their broadly permissioned accounts.
6) Putting Locally governed files at risk
A hacker will frequently focus their attack on company assets that are stored locally on machines. These are not governed by data retention policies, backup roles, data identification classification processes, and group policy enforcement mechanisms. It is not uncommon for an administrator to enforce strict company storage policies with private or public cloud synchronization.
Managing Entitlements – The Verdict
The above represent just a few of the potential activities that a hacker will use to ruin your organization. The first step to remedy existing activity is to be proactive in protecting your assets governed by permissions over your unstructured data (Active Directory, SharePoint, etc.). To do this, you can use discovery tools that pull back the complicated layers of understanding your security profile. To expose resources and how they are permissioned. To gain understanding of permission inheritance and apply management policies that will cause regular review and proactive measure to mitigate future risk.
When it comes to data governance, access to sensitive data should be exclusive. That is, resources should be accessible by the fewest people necessary. Permissions should be the lowest possible for performing a role or function. An understanding of the data and entitlements is critical before an organization makes the above decisions.
GroupID by Imanami
Leader in Active Directory and IAM, Imanami is a ‘customers-love-us’ Software Solutions Company that has been writing the book on Group, User, and Entitlement Management for over 20 years.
Imanami is a solution-first IAM company – empowering organizations to better manage their Active Directory against Groups, Users and Entitlements.
For more details, click here.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.

