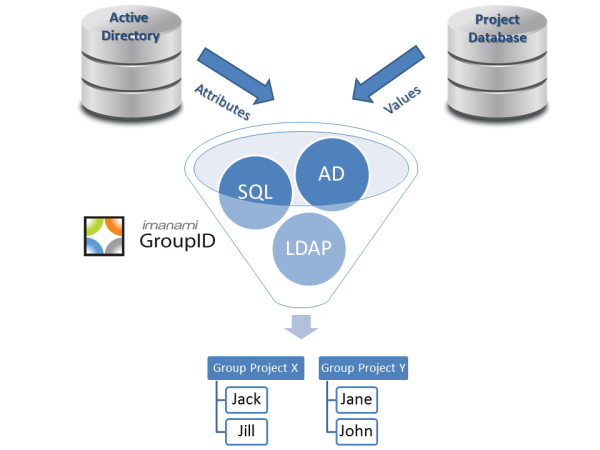
Active Directory Group Hijacking Solved with Workflow
The example we gave when designing the group hijacking feature for GroupID was absurd. Say you owned an Exchange distribution list designed to discuss cookbooks and somebody else owned a distribution group designed to discuss the Anarchist Cookbook…very different sets of users with most likely a very different set of discussions. If the owner of the…