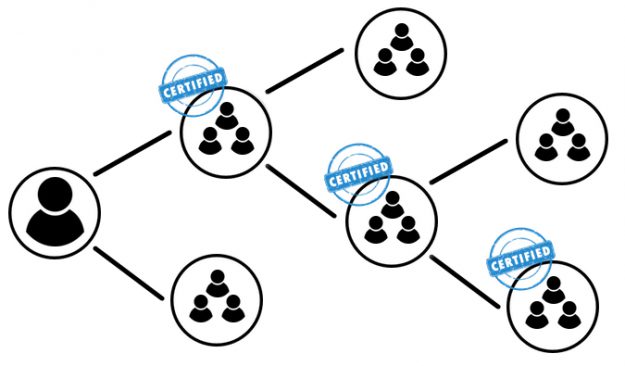
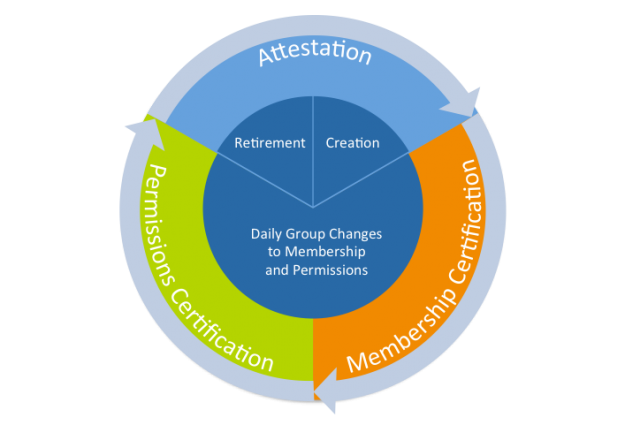
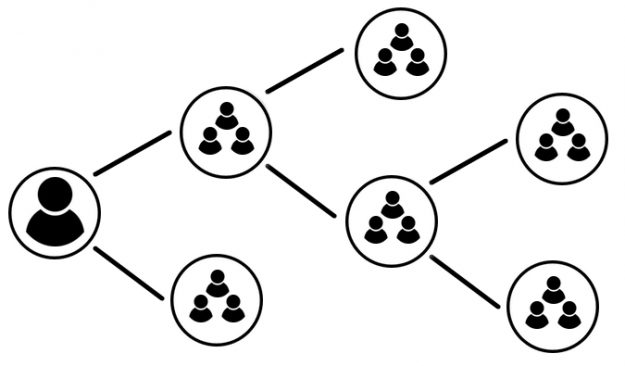
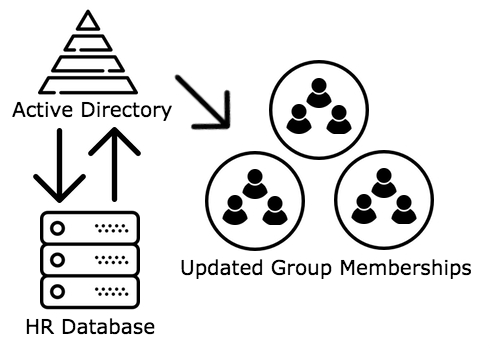
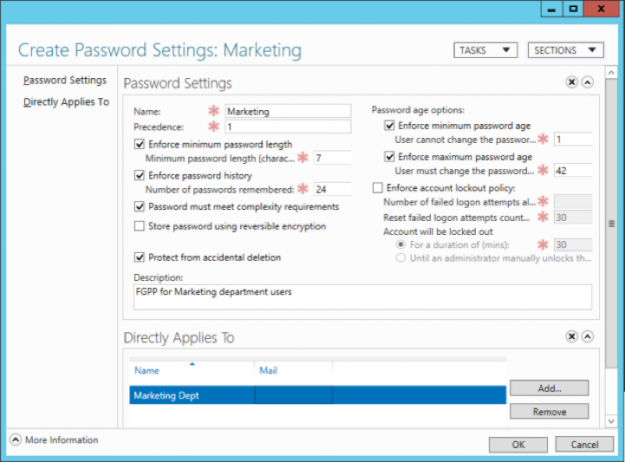
AD Group Lifecycle Management – Certifying Permissions
One of the greatest faults in the architecture of AD is the complete lack of documenting when someone assigns permissions to it. You know what I’m talking about – you’re in SharePoint, or on a file server and you add some permissions to a resource. You grab a list of users and groups from AD,…