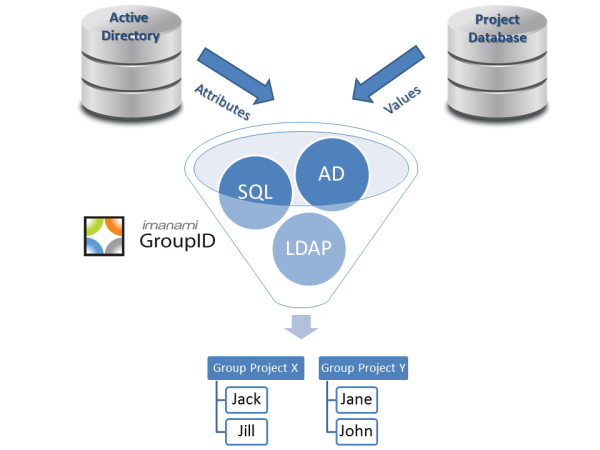
Intelligently Organize Domain Computer Objects in Security Groups
Just as Active Directory has a user object for each network user, it has a computer object for each computer in the domain. These objects are treated as an account. As with user accounts, computer accounts provide a means for authenticating and auditing the computer’s access to the network and its access to domain resources.…