In any organization, there are numerous users’ objects including employees, managers, and clients, in active directory and azure active directory, with certain attributes assigned to them within HR database. All these users need to have appropriate active directory permissions within organization’s identity and access management framework, to allowing employees access resources on the network, so they can do their jobs effectively. They cannot be held back by needing to request access each time they need something. On the same note, organizations need to protect private or personal data, sensitive resources, and vital security information—both from internal threats and from cyberthreats such as Ransomware Attacks.
Read More: Ransomware Attack in Active Directory & Azure AD
This process should be managed by appropriate active directory user provisioning.
Provisioning is the process of making information technology (IT) resources available to users.
Levels of Provisioning
Depending on your organization’s needs, provisioning or deprovisioning can be defined generally at the four levels:
- Network
- Server
- Application
- User
This article elaborates on provisioning at user level.
What is User Provisioning & Deprovisioning in Active Directory?
Provisioning
User Provisioning (or user account provisioning) in Active Directory and Azure AD is the process of granting privileges and active directory permissions to users or groups objects, based on role (a user attribute within HR database). It involves creation, modification, and deletion of user accounts and permissions with in ad.
These identity management actions take place whenever there is a change or addition of in the attributes of user objects in a HR database.
Deprovisioning
User Deprovisioning is the process of revoking privileges and access rights of a user or a group within active directory to ensure they no longer have access to company resources.
Now that we are clear about user provisioning & deprovisioning.
Main Kinds of User Provisioning
There are four main kinds of user provisioning:
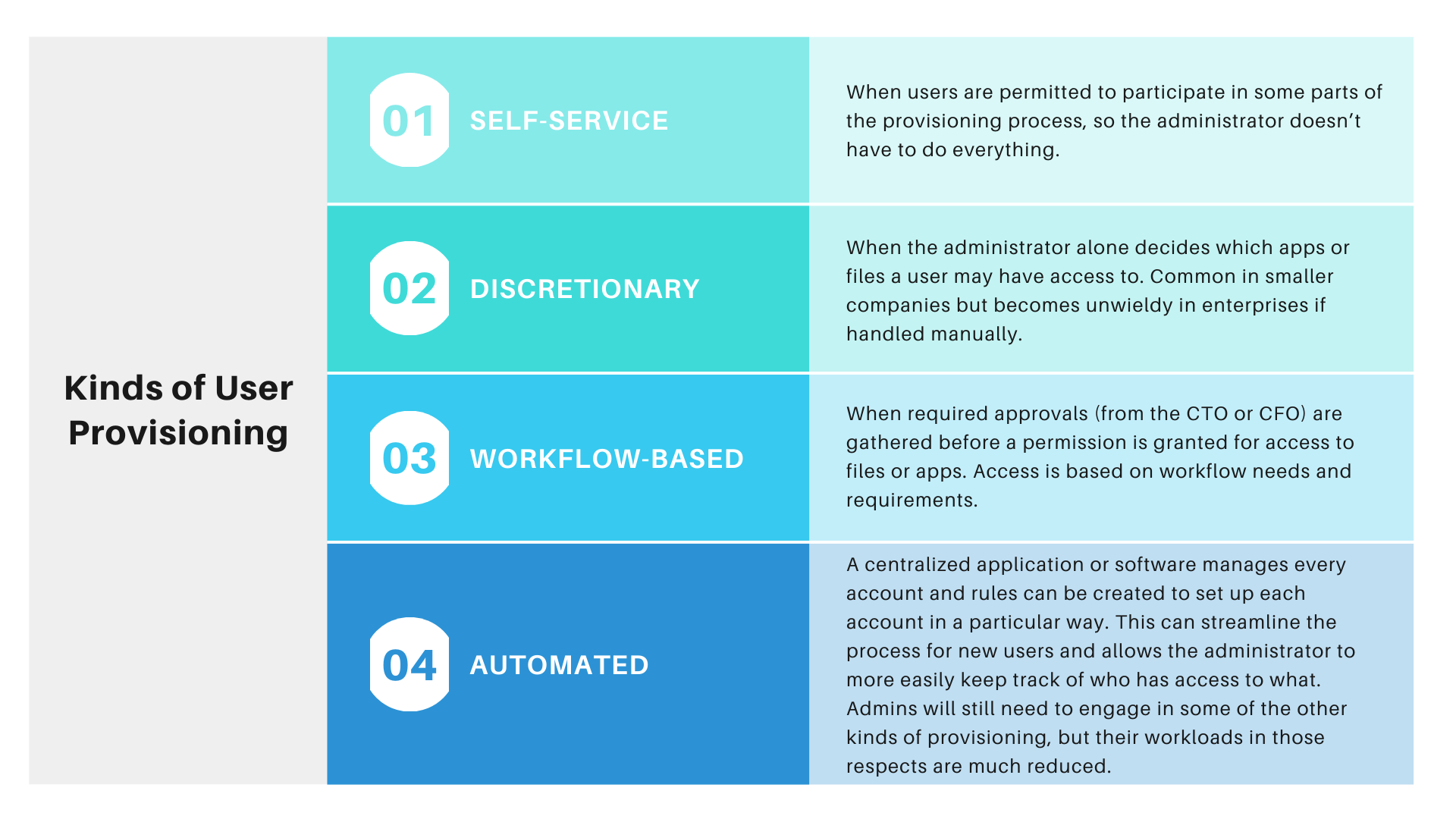
Self-Service:
It refers to when users are permitted to participate in some part of provisioning process, so the administration doesn’t have to do everything.
Discretionary:
It refers to when system administrator alone decides which apps or files a user may have access to.
Workflow Based:
When required approvals from CTO or CFO are gathered before a permission is granted for access to files or apps. Access is based on workflow needs and requirements.
Automated:
Rules can be created in each account within centralized application, thus streamlining the process new users and enabling the administrator to keep tracks of access with respect to each user object.
Let’s talk about Automated Provisioning!
In Automate provisioning, every account is added in the same manner through a centralized management application interface. This streamlines the process of adding and managing user credentials and provides administrators with the most accurate way to track who has access to specific applications and data sources. Although provisioning and identity management processes are the same, the extent and type of provisioning varies greatly among different users (e.g., patients, clinicians, customers, and partners).
Read more: Automated Provisioning Machine for Active Directory
Benefits of Automated User Provisioning
When an employee leaves the organization, all their accounts and access should be immediately removed, to prevent an unused identity being potentially exploited by either former employees or any other outside factors, thus timely user deprovisioning is extremely important for organization to maintain its security.
Automated provisioning makes the manual processes of onboarding and offboarding users automatic. In organizations both big and small, automated user provisioning frees up IT and HR to work on more strategic tasks, prevents gaps in security by minimizing the impact of human error, and provides better user experiences.
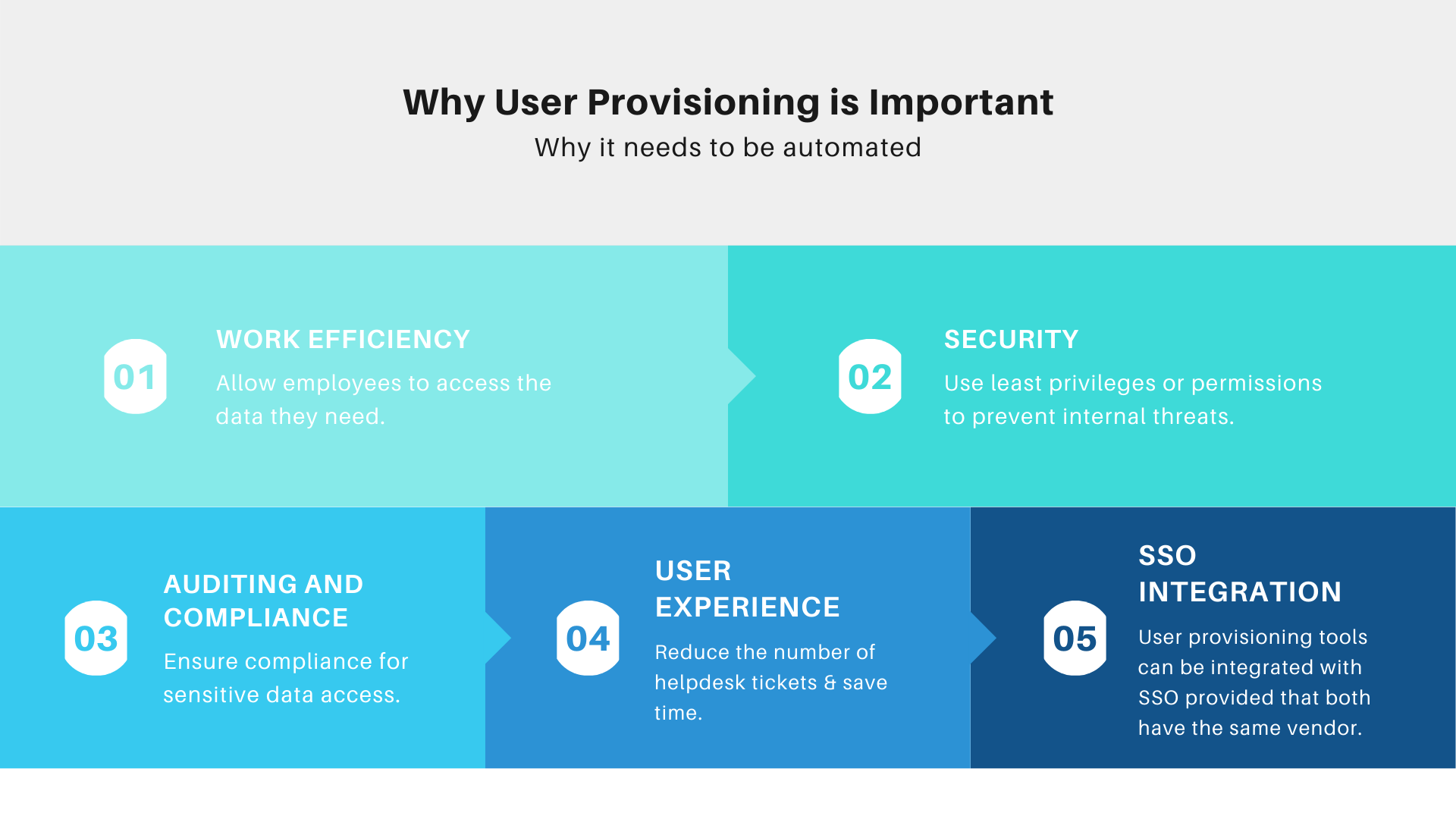
Automate user provisioning provides organization with the following benefits:
Work Efficiency:
Allow employees to access data they need
Security:
Use least privileges or permission to prevent internal threats
Auditing & Compliance:
Ensure compliance with sensitive data access
User Experience:
Reduce the number of helpdesk tickets & save time
SSO (Single Sign-On) Integration:
User provisioning tools can be integrated with SSO provided that both have the same vendor
Automated User Provisioning and Deprovisioning Enhances Security
Automated user provisioning helps keep your company secure by ensuring:
- Employees have access only to the apps they need.
- Whenever an employee leaves, their access is automatically removed for all connected applications.
- All existing user sessions are removed to reduce security risk.
The risk of costly security breaches for companies who fail to provision and deprovision, properly or quickly, is huge: the average cost of a data breach is $3.86 million per breach in the U.S. As a result, breached companies often underperform the market for years following a major breach.
Read more: Active Directory User Provisioning made easy
From the Diaries of our SME
When Microsoft first released Forefront Identity Manager (FIM), they described an alarming statistic:
“On average, every new user needs to be added to 16 directories upon hire; upon fire, the average user is only taken out of 9 directories”
If the above statistic is true, then the average user is still floating around in 7 directories after leaving a company (assuming they mean directories and databases). To be fair, these might be completely benign data repositories like Active Directory, the badge system, payroll, or who knows what – or chances are they could be important.
One of our IAM specialists said:
“I just know that I want ex-users completely deprovisioned to the point they cannot do anything on my network. I can’t imagine that MSFT meant they were inactive users on those directories because our own Active Directory research shows something else alarming. It takes an average of 9 days for organizations to deprovision a user from Active Directory after termination.”
He told us:
“9 days of access, what could a bad guy do with that? Steal all your CRM data? Book a flight to Paraguay? Steal source code? Plant a virus? Prank call customers from within your phone system? This is a big deal.”
The obvious answer is to create an automated provisioning and deprovisioning process. So, it leads to the following question:
How to Setup Automate User Provisioning in Active Directory?
One of ways that an effective Automate Provisioning and Deprovisioning can be achieved is to employ GroupID Synchronize, that enables you to create bi-directional provisioning and deprovisioning jobs with almost any database or directory as a source or destination. GroupID does not use a meta-directory, instead writing directly to the source DB/directory.
It starts with finding the authoritative source (usually HR) and go from there. Once you identify all the systems where a user needs to have accounts, simply provision them using GroupID following. IT Pros, during their hopefully long and productive career, use GroupID to synchronize changes in their identity (department, shoe size, title, etc.).
Once they are terminated, use the reverse of the provisioning jobs and deprovision them from the destinations. You can even daisy chain these jobs to be sure that all data is passed along (for example, HR doesn’t have an email address until provisioned in Active Directory/Exchange).
Steps to Setup Automated Provisioning & Deprovisioning Jobs via GroupID Synchronize
- GroupID Synchronize will require a Source and Destination Provider for offering Automation around Onboarding and Off-Boarding of Users.
(Source feed can be from a Database like SQL, Oracle, ODBC, Access, Excel Sheet or a Flat file like a CSV / TXT (Comma Delimited) - For Destination, it primarily uses Active Directory, we can use other types of Destination providers as well to move data from Active Directory into other repositories.
- Select a type of object to Sync “User” / “Mailbox” or “Contact”
- Based on Template, Mandatory fields become visible but the option is available to add any attribute from the destination provider for Synchronization against each User.
- Field Mappings allow putting Source Fields into Destination Fields (attributes). We require a primary key to define unique Records.
*Field Map also offers the ability to modify source data before its synchronized in destination provider on-the-fly. This will be validated for each individual record and offer Automation to help with Data Normalization / Correction / Modification / Validation - Specify a name for the Job (Nothing to do with the flow)
- Run or Preview your job to verify the changes before they are actually committed.
- Create a Schedule to run the job based on desired update frequency.
Rinse-Repeat for Creation / Updating / Disable / Delete Jobs around records.
How to Streamline User Provisioning & Deprovisioning Process?
Once you have implemented the user provisioning solution in the organization, make sure you monitor it on a monthly, quarterly, or yearly basis. Track the number of user provisioning requests handled, the time required to address such requests, internal audit findings, and user experience level to improve the process continually.
Learn more: 3 Steps to Gaining Control and Governance over Permissions
Protect Your Information Assets from Unauthorized Access!
No business will survive with 58% productivity every time a user changes or starts a position. Think about internal and external turnover in your environment and think of how your business will prosper with that lost 42% productivity just by managing permissions and completing the user provisioning process.
If you fear that there might be ex-users sitting in 7 directories on your network, sign up for a free trial of GroupID today and don’t take 9 days to do it!
Learn more about how to securely manage your active directory, Azure active directory groups and avoid costly mistakes.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.

