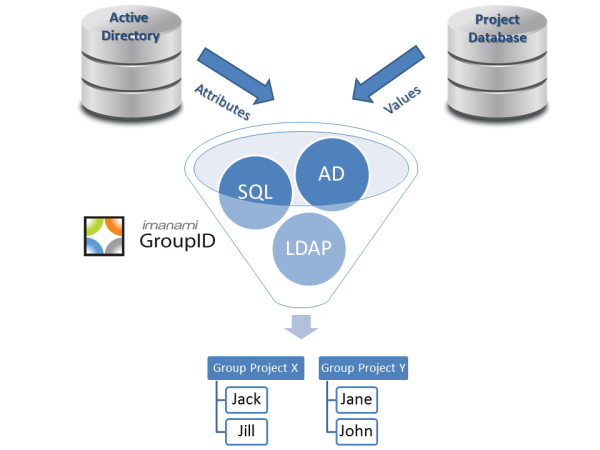
Types of Active Directory Groups & Scopes
What are Active Directory Groups? Active Directory groups are methods for collecting users, contacts, computers, and even other groups’ objects within Active Directory so that you can manage the objects in the group as a single unit. Objects in Active Directory Groups Objects that belong to a particular group are referred to as group members.…