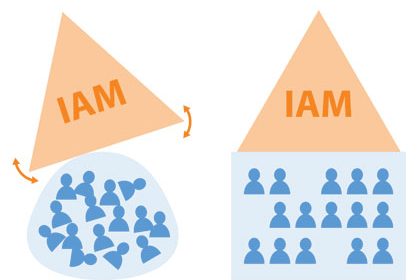
Implementing IAM: Don’t Get Ahead of Yourself
As your organization has grown, so has your IT infrastructure. You now have so many systems requiring some level of authentication, and so many protected data sets that need to be protected, that your organization has come to the realization that it’s time: You need to implement IAM. At first, this can be an exciting…